Incident Response
Incident Response & Security Operations Center (SOC) Operations
Information note: The information below is provided for informational purposes only. It helps the client better understand available approaches and technologies for responding to cyber incidents, supporting the selection of appropriate solutions to protect the vessel.
Important remark: This module describes the highest level of protection, using modern technologies for high-risk environments (e.g., high-profile owners or vessels operating in tense regions). In practice, we assess threats for each client and select the optimal option—from basic measures (automated monitoring + a baseline incident response plan) to a full capability—avoiding unnecessary cost while maintaining robust security.
Module Overview
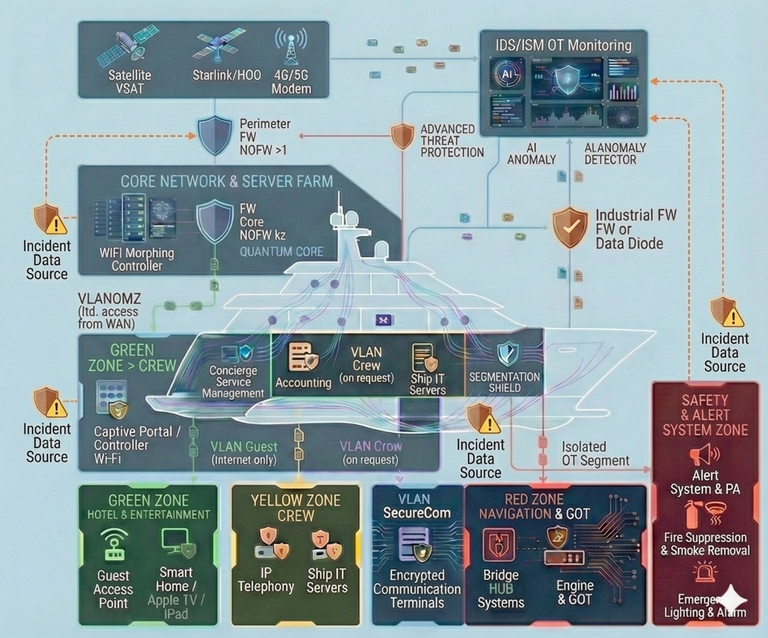
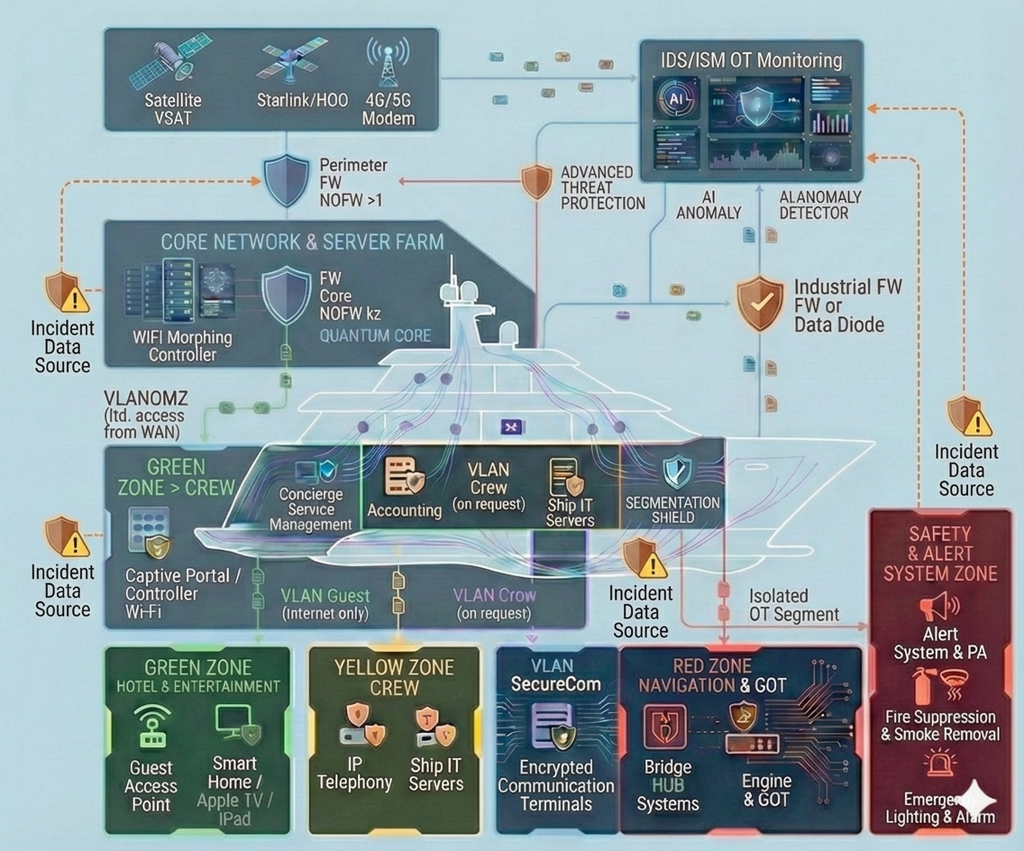
The “Incident Response” module is an active component of a vessel’s cyber defense system. It provides continuous oversight and rapid action when threats arise. Our Security Operations Center operates 24/7, combining expert analysts with AI-driven automation to detect and remediate issues quickly.
In maritime environments—where connectivity may be intermittent and operations are often autonomous—the module follows a “Detect, Respond, Recover” approach to minimize operational disruption. It analyzes telemetry across all zones (Red, Yellow, Green), anticipates emerging issues, and automatically contains threats. The module integrates with AI-based anomaly detection, the Quantum Core (post-quantum resilience), and external threat intelligence. This strengthens resilience against evolving risks such as zero-days or coordinated navigation-targeted attacks.
1. 24/7 monitoring and detection
The SOC functions as the central node, fusing onboard sensors with external services to maintain a unified operational picture.
- AI-assisted threat hunting: Continuous analysis of event logs from intrusion detection (IDS/ISM), OT Cyber Sensors, and navigation sources. Machine learning models identify abnormal patterns (e.g., unusual NMEA exchanges or RF anomalies) and forecast risk using vessel-specific historical baselines.
- Real-time alerting: Automated, rule-based signals (e.g., SIEM using platforms such as Splunk) and behavioral analytics. Upon detection (e.g., GPS signal manipulation), immediate notification is sent to the crew via secure channels (VLAN SecureCom) and to the external SOC for next steps.
- Threat intelligence integration: Automated ingestion of threat data (e.g., MITRE ATT&CK and specialized sources), with AI-driven analysis to anticipate likely attack paths.
- Secure, quantum-resilient communications: All notifications are protected using quantum-resistant algorithms (CRYSTALS-Kyber) to reduce interception risk—even in open-sea conditions.
2. Rapid action and containment
When an issue is identified, the module triggers automated and crew-led procedures to reduce impact.
- Automated response playbooks: SOAR-driven runbooks—for example, isolating an affected zone (SDN switches block traffic), switching to backup modes (inertial navigation for positioning), or isolating endpoints via EDR.
- Tiered escalation: Level 1 (automated, < 1 minute) — block IPs/processes; Level 2 (onboard crew, < 5 minutes) — manual verification; Level 3 (external SOC, < 15 minutes) — remote analysis via VLAN OMZ.
- Insider threat controls: Automated validation of crew actions by correlating access events (from the Access Control module) with anomalies, including the ability to temporarily lock biometric factors.
- Cyber-physical response actions: For bridge-related issues (e.g., spoofing), linkage to autopilot safe mode, targeted notifications (as required), and activation of drone-defense measures.
3. Recovery and post-incident review
Emphasis is placed on rapid restoration of normal operations and extracting lessons learned.
- Automated recovery procedures: Restore from isolated backups (secured by the Quantum Core with immutable records), with integrity validation (hash checks) before reintroduction.
- Digital forensics toolkit: Tools such as Volatility for memory analysis and forensic review (including ECDIS), with secure evidence preservation.
- Lessons learned repository: AI-assisted analysis to update rules and models, with periodic reporting for the owner.
- Compliance reporting: Automated documentation aligned with IMO MSC.428(98) and GDPR expectations, recording actions taken.
4. Software-based safeguards against unauthorized access
This section strengthens incident response by preventing escalation through software barriers and integrates with control layers for proactive action.
- RBAC/ABAC in incident context: Temporary roles for responders (e.g., “Incident Specialist”) and attributes (e.g., access only during an active alert).
- MFA and SSO for SOC tooling: Mandatory MFA for SIEM/SOAR consoles, with session revocation on suspicion.
- Data encryption and key management: Incident data protected with AES-256 and post-quantum cryptography; keys stored in the Quantum Core HSM with scheduled rotation.
- WAF and EDR in action mode: Automated EDR isolation and dynamic WAF rule updates driven by threat intelligence.
- Logging and SIEM integration: Immutable logs and AI-driven analysis to support root-cause investigation.
5. Specialized validation: “Incident Response Exercises”
Comprehensive readiness drills are conducted every three months.
- Tabletop exercises: Scenario walkthroughs (e.g., ransomware on ECDIS) involving the crew and the external SOC to rehearse plans.
- Practical exercises: Controlled attacks (e.g., Red Team simulation of spoofing) conducted in port, with measurement of response time and containment effectiveness.
- After-action review: Identification of gaps and updates to ML models and detection rules.
- Compliance validation: Assessment against NIST SP 800-61 and maritime requirements.
- Toolchain testing: Simulated attacks against response systems (e.g., DDoS on SIEM), plus SAST/DAST for automation and control quality assurance.
Integration with the overall system
- AI-driven anomaly detection linkage: exchange of incident telemetry to trigger actions and continuously improve detection.
- Data Diode linkage: one-way export of investigation data to the external SOC with no inbound compromise path.
- Quantum Core linkage: protection of communications and keys against quantum-era threats.
- Navigation and Access Control linkage: automated bridge containment actions and access restrictions during incidents.
This module makes threats manageable by providing not only response, but continuous improvement of defenses. We recommend an initial exercise to tailor the workflows to your vessel.
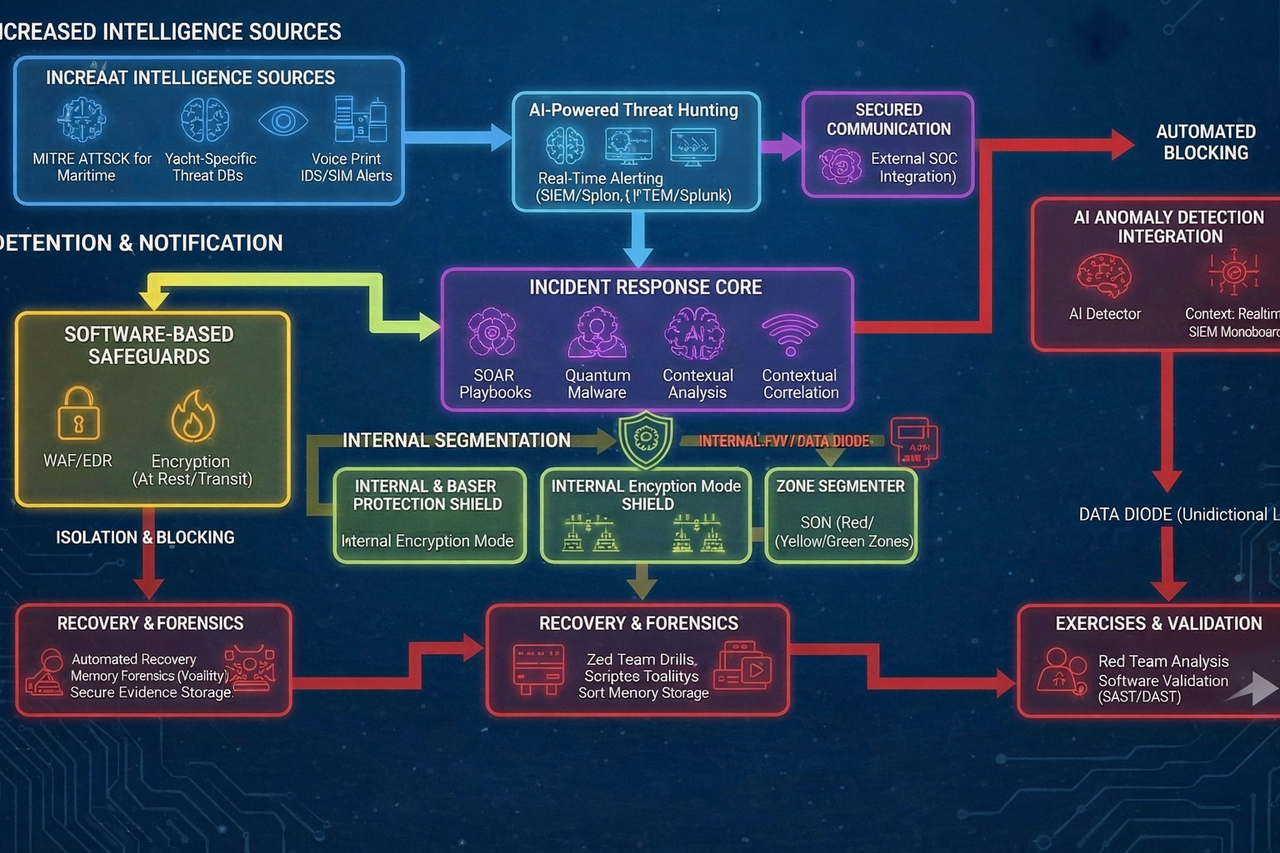
Flowchart: Operating Logic of Incident Response Systems
1. External Layer: Threat detection and signal intake
- Components: Data from external sources (e.g., MITRE ATT&CK mapped to the maritime domain, specialized yacht threat databases), and alerts from onboard systems (IDS/ISM).
- Function: Collect initial threat and anomaly signals for analysis.
- Flow: Entry point for all external and internal alert signals.
2. Security perimeter and initial response
- Components: AI-assisted threat hunting (ML models, e.g., PyTorch-based), real-time alerting (SIEM, e.g., Splunk).
- Function: Rapidly identify issues (e.g., GPS signal manipulation) and deliver notifications via secured channels (VLAN SecureCom).
- Components: Encryption with quantum-resilience (CRYSTALS-Kyber), integration with an external Security Operations Center (SOC).
- Function: Automatic initial containment upon suspicion; notifying AI workflows for subsequent steps.
- Feature: Isolation from external attacks, including interception attempts at sea.
3. Core Layer: Analysis and coordination
- Components: Automated playbooks (SOAR), multi-tier escalation (Levels 1–3: automated, crew-led, external SOC).
- Function: Analyze signals (including correlation with access/identity data), route actions, and stop threats in real time (e.g., isolating zones via SDN).
- Components: AI detector, zone sensors, SIEM dashboards.
- Function: Central “brain” for real-time analysis; linkage to a Data Diode for one-way information transfer.
4. Internal segmentation: Protecting layers and procedures
Ingress enforcement: Role-based access control (RBAC/ABAC) / Encryption.
TRACK A: Software and automated actions (Software layers)
- Systems: MFA, SSO, WAF, EDR.
- Status: Asset-level access isolation (servers, databases, industrial devices), automatic process containment.
TRACK B: Defense against insider and cyber-physical threats (Internal and physical layers)
- Systems: Crew activity verification, temporary biometric lockouts.
- Additional: Response to cyber-physical threats (autopilot safe mode, drone defense).
- Systems: SDN to isolate Red/Yellow/Green zones and prevent threat propagation.
5. Critical infrastructure: Recovery and validation
TRACK C: “Recovery & exercises” zone (Non-intrusive validation)
Critical barrier: Isolated environments for exercises / simulators (isolated test environments).
Principle: Safe methods that do not affect vessel operations. Exercise data is exported for analysis, but does not touch live systems.
- Systems: Automated recovery procedures, investigation tools (Volatility for memory analysis, secure evidence storage).
- Status: Full recovery with integrity validation.
- Systems: Tabletop and practical drills (Red Team attack simulation), after-action review, software checks (SAST/DAST).
- Function: Train crew and systems, align with standards (NIST SP 800-61, IMO), and improve readiness.