Access Control
Access Control & Identity Assurance
Information note: The information below is provided for informational purposes only, to give the client a comprehensive understanding of available access protection measures and technologies, supporting an informed selection of optimal solutions to secure the vessel.
Important remark: The module described below represents the highest achievable level of protection, integrating advanced technologies for the highest-risk scenarios (e.g., high-profile owners or vessels operating in areas of geopolitical tension). In practice, we perform a client-specific threat assessment and select the optimal option—from a baseline set of controls (biometrics + RBAC) to full deployment—to avoid over-engineering and optimize cost without compromising security.
Module Overview
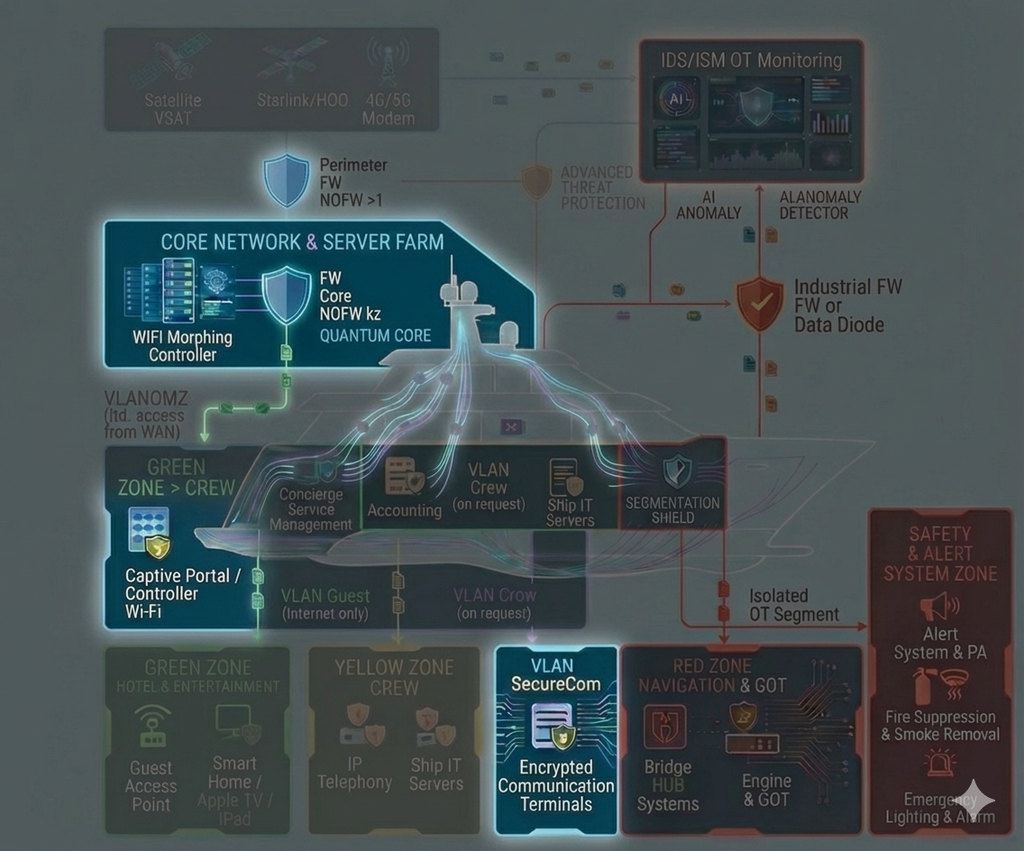
The “Access Control & Identity Assurance” module is a core element of a vessel’s Zero Trust architecture across the Red, Yellow, and Green zones. It eliminates the concept of a “trusted network” and enforces the “Never Trust — Always Verify” principle at every layer: logical, biometric, physical, and software.
The system is built around continuous authentication and micro-segmentation, where every access request—whether entering a server room, connecting to ECDIS, or launching a critical application—undergoes multi-factor, real-time verification. The module integrates with AI Anomaly Detection and Quantum Core, providing post-quantum cryptographic resilience and behavioral analytics to preemptively block insider threats and credential compromise.
1. Logical Access Control (Zero Trust Access Fabric)
Implementation of a full Zero Trust model with dynamic access policies.
- Continuous Session Validation: Each session (local or remote) is re-validated every 60–300 seconds using context: vessel geolocation, time of day, device type, user behavioral profile, and current risk score (computed by AI).
- Policy Enforcement Point (PEP): Distributed policy enforcement across the entire stack—from Wi-Fi Morphing controllers and SDN switches to hypervisor-level virtualization controls and kernel-level workstation protection.
- Just-in-Time Access: Red Zone access is granted only for the minimum necessary time window (from 5 minutes to 2 hours) and only after explicit approval by two authorized parties (Captain + Senior Security Officer, or Owner + CISO).
- Quantum-Resistant Authentication Protocols: Use of post-quantum algorithms (CRYSTALS-Kyber, CRYSTALS-Dilithium) for all sessions, including remote access via VLAN OMZ and SecureCom.
2. Multi-Modal Biometric Authentication (Multi-Modal Biometrics)
Passwords are removed as the primary factor. Passwords are prohibited for all systems above the Green Zone.
- Palm vein readers (Fujitsu PalmSecure) — exceptionally high accuracy and extremely difficult to spoof (sub-dermal vascular pattern recognition).
- 3D cameras with IR illumination and liveness detection — prevents photo/video attacks and silicone mask spoofing.
- Continuous behavioral analytics: keystroke dynamics, mouse/trackpad patterns, device tilt angle, gait analysis (via sensors embedded in accommodation and bridge flooring).
- Voice biometrics for critical commands (e.g., confirming a course change or server-room access).
- Molecular touch sensor layer on doors and terminals that reads DNA traces from skin contact (VIP-grade assurance level).
Fail-safe mode: Any doubt in biometric validation triggers immediate access lockout and transitions Red Zone systems to autonomous mode with physical locks engaged.
3. Physical Security for Server Rooms and Critical Spaces (Physical Security Perimeter)
Server rooms, the bridge, engine room, and Quantum Core compartments are protected to a standard exceeding typical bank vault requirements.
- Two-door mantraps with weight-based verification and metal/explosives detection.
- Biometric gateway: entry only after passing two biometric steps using different modalities (palm vein + facial).
- Server-room walls: composite panels with Kevlar core and embedded vibration sensors.
- Seismic and acoustic sensors + internal laser grids.
- Autonomous power (72+ hours) and a Novec 1230 fire suppression system with vacuum oxygen removal.
- Prevents a second person from entering “on the heels” of the first.
- One-time passage: after entry, biometrics are locked for 30–180 seconds.
- External RF detectors and kinetic interceptors to defend against reconnaissance drones attempting to scan secure spaces through portholes or deck structures.
4. Software-Based Access Safeguards
This section focuses on software mechanisms that prevent unauthorized access to the vessel’s information and computing infrastructure, including servers, databases, navigation systems, and OT devices. Controls are built on Least Privilege and Defense-in-Depth principles, integrating with the broader architecture for monitoring and automated response.
- Dynamic role assignment (e.g., “Captain” — full bridge access; “Crew” — restricted to Green Zone). ABAC adds attributes (time of day, alert status) for contextual enforcement (e.g., ECDIS access blocked while alongside unless the owner approves).
- Implemented via a centralized Identity Provider (IdP) compatible with SAML/OAuth 2.0 and integrated with Active Directory or maritime-grade equivalents.
- Mandatory MFA for all software interfaces (e.g., monitoring dashboards, SSH server access) using hardware tokens (YubiKey) or secure-device push approvals.
- SSO enables seamless transitions across systems without repeated logins, with session revocation upon anomaly detection (e.g., via IDS/ISM integration).
- All stored data (server SSD/HDD, VDR databases) is encrypted using AES-256 and post-quantum algorithms. Keys are managed via an HSM within Quantum Core, with automatic rotation every 90 days.
- Inter-system traffic (e.g., radars to ECDIS) is protected with TLS 1.3 and forward secrecy, preventing MITM attacks.
- Web Application Firewall (WAF) for interfaces (e.g., concierge service portals) with rules against SQL injection, XSS, and API abuse.
- EDR (Endpoint Detection & Response) on all compute nodes, including legacy systems (e.g., Windows Embedded on the bridge), with suspicious process quarantine and AI-assisted threat hunting.
- Full logging of all access events (syslog, auditd) to a central SIEM integrated with OT monitoring. Logs are stored in an immutable (blockchain-like) format to prevent tampering.
- Automated alerts for unauthorized attempts (e.g., SSH brute-force) with IP/device blocking and CISO notification.
5. Specialized Audit: “Zero Trust Verification Trials”
A comprehensive access control audit is performed annually and after every incident.
- Red Team physical penetration: Attempts to breach physically using social engineering, forged biometrics, drones, etc.
- Biometric spoof testing: Testing against known spoofing methods (3D-printed veins, deepfake video, silicone masks, voice synthesis).
- Zero Trust policy audit: Automated verification of 100% of access policies with attack simulation (Golden Ticket, Pass-the-Hash, privilege escalation).
- Insider threat simulation: Modeling a crew member with legitimate access attempting to exceed authorized privileges.
- Software safeguards validation: Testing software controls—simulated attacks on RBAC/ABAC, MFA bypass, encryption, and logging, including code vulnerability assessment (SAST/DAST) and alignment with IMO cybersecurity standards.
Integration with the overall architecture
- Link to AI Anomaly Detection: all access events (successful and failed) are streamed in real time for correlation with network and navigation anomalies.
- Link to Data Diode: physical and logical access logs are exported unidirectionally for analysis, with no possibility of backflow.
- Link to Quantum Core: post-quantum protection for identity keys and certificates.
- Link to the Navigation module: bridge and ECDIS access requires not only biometrics, but contextual validation (vessel not alongside; no active alerts).
This module turns access control from a “point of entry” into an active defensive layer that detects and neutralizes threats before they can materialize.
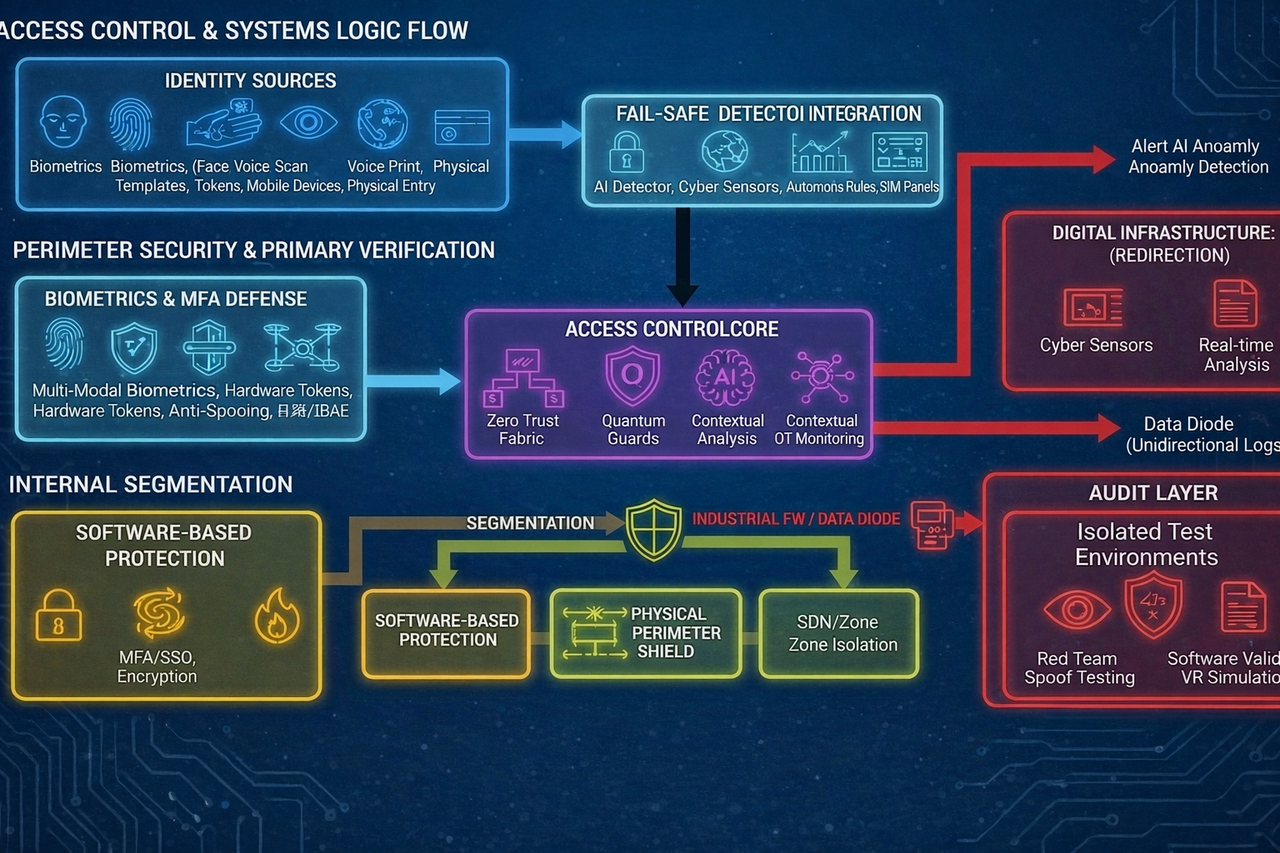
Flowchart: Operating Logic of Access Control Systems
1. External Layer: Access Requests & Identity Input
- Components: Biometric factors (face, palm vein, voice, behavioral signals), devices (YubiKey tokens, mobile devices), physical entry points (doors, terminals).
- Function: Collect initial access requests to the vessel’s systems, spaces, or data.
- Flow: Ingress point for all authentication signals.
2. Security Perimeter and Primary Verification
- Components: Multi-modal biometrics (Palm Vein, 3D Facial, Behavioral Analysis, Voice Print, DNA-Touch), MFA with hardware tokens.
- Function: Physical and software-level filtering of requests to detect and block forgeries (anti-spoofing), verifying liveness and contextual signals.
- Components: Automatic lockout on uncertainty, transition to Red Zone autonomous mode.
- Function: Automatic denial on anomalies, with alerting to AI Anomaly Detection.
- Feature: Isolation from external threats, including social engineering and forgery attempts.
3. Core Layer: Policy Processing and Monitoring
- Components: Zero Trust Access Fabric (Continuous Session Validation, PEP, Just-in-Time Access), quantum-resistant protocols (CRYSTALS-Kyber/Dilithium).
- Function: Dynamic policy evaluation (RBAC/ABAC), access routing, and real-time context-based anomaly detection (geolocation, time, risk score).
- Components: AI detector, cyber sensors across zones, SIEM dashboards.
- Function: The “brain” of identity assurance. Ingests data (logs/alerts) from the perimeter and endpoints for real-time analysis; integration with a Data Diode for unidirectional log export.
4. Internal Segmentation: Protecting Access Layers and Interfaces
Ingress enforcement: RBAC/ABAC / Encryption Enforcement.
TRACK A: Logical and software access (Zero Trust Layers)
- Systems: MFA/SSO, Encryption at Rest/Transit (AES-256 + post-quantum), WAF/EDR.
- Status: Segmented access to infrastructure assets (servers, VDR repositories, OT devices), process quarantine.
TRACK B: Physical & contextual access (Physical & Contextual)
- Systems: Mantraps, gateways, anti-tailgating controls, drone defense.
- Additional: Multi-layer compartment protection (vibration sensors, laser grids, autonomous power).
- Systems: SDN to isolate Green/Yellow/Red zones and prevent lateral movement.
5. Critical Infrastructure: Audit and Verification (Audit Layer)
TRACK C: “Audit” zone (Non-Intrusive Verification)
Critical barrier: Isolated test environments / simulators (Isolated Test Environments).
Principle: Non-intrusive methods that eliminate the risk of access disruption. Audit data is exported for analysis but does not affect live systems.
- Systems: Red Team penetration testing, biometric spoof testing, policy audit, insider simulation.
- Status: Full compromise assessment.
- Systems: Software safeguards validation (SAST/DAST), compliance checks (IMO standards).
- Function: Testing system and crew response, including attack simulations to assess resilience.
