Navigation Safety
Navigation Systems Protection: Navigational Integrity & Spectrum Defense
Information note: The information below is provided for informational purposes only, to offer a comprehensive overview of available measures and technologies for protecting a vessel’s navigation systems. This enables an informed selection of solutions tailored to specific risks and operational needs.
Important remark: The module described represents the highest achievable level of protection, integrating advanced technologies for high-risk scenarios (e.g., vessels operating in elevated-threat areas or carrying high-value assets). In practice, we conduct a client-specific threat assessment and select the optimal option—from baseline measures (signal filtering + basic hardening) to full deployment—to avoid over-engineering and optimize cost without compromising safety.
Module Overview
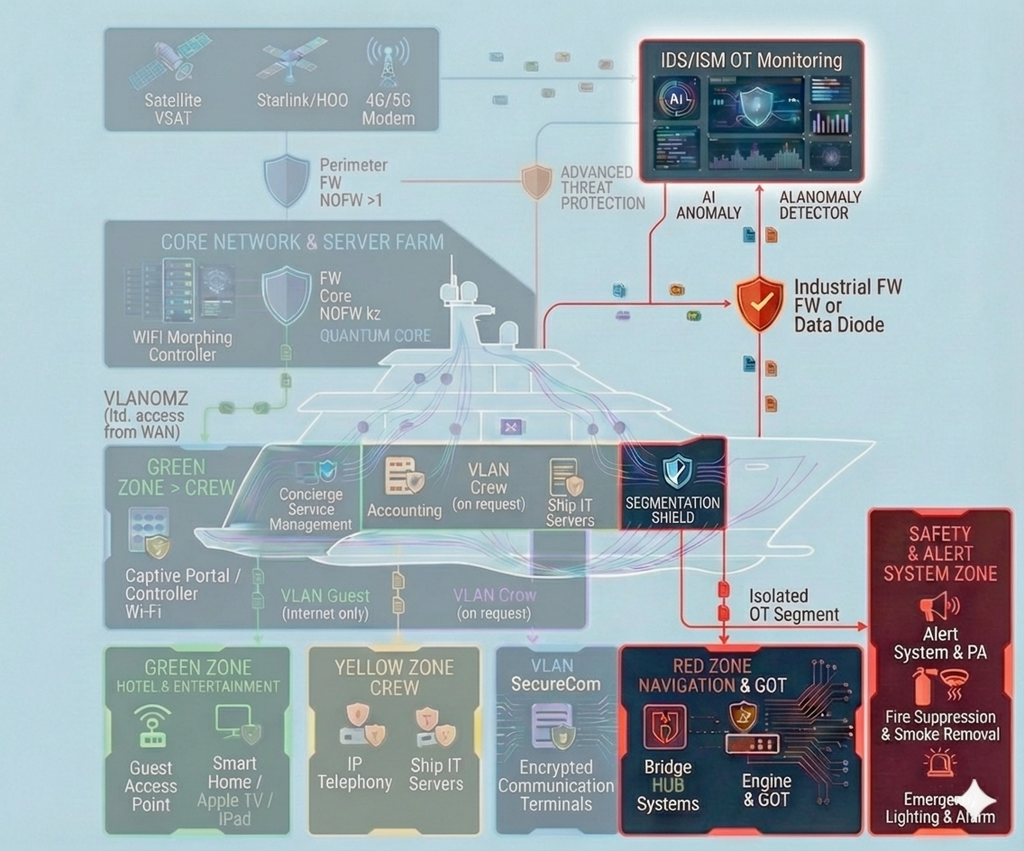
The “Navigational Integrity & Spectrum Defense” module is a critical component of the vessel cybersecurity architecture’s “Red Zone” (RED ZONE). It focuses on ensuring the trustworthiness of vessel positioning and protecting against spectrum-level threats such as GPS spoofing (signal manipulation), jamming (interference), and external cyberattacks targeting navigation interfaces.
In an era of escalating cyber-physical threats, traditional GNSS (Global Navigation Satellite Systems) become vulnerable entry points for adversaries. The module addresses fundamental weaknesses: excessive trust in external signals and the exposure of legacy protocols (e.g., NMEA). Protection is implemented through a multi-layer Defense-in-Depth strategy: physical signal filtering, cryptographic reinforcement, software monitoring, and integration with AI-driven anomaly detection. This ensures operational continuity even under complete satellite signal loss, with automatic failover to autonomous modes.
The module aligns with Zero Trust principles, integrates a Quantum Core for post-quantum cryptography, and connects to global monitoring (IDS/ISM OT Monitoring), making the system resilient against evolving threats—including drone-based attacks or AI-generated spoofing.
1. Spectrum Defense & GNSS Assurance
Protection starts at signal ingress, preventing false data from entering the vessel network.
- Adaptive CRPA antennas (Controlled Reception Pattern Antennas): Phased-array installation that dynamically suppresses low-elevation signals (typical of land-based or drone-enabled attacks), focusing on satellite signals from higher elevation angles. Integrated with IMU (Inertial Measurement Units) to correlate inertial data and validate integrity.
- GNSS Firewall (Navigation Firewall): A hardware module positioned between antenna and receiver for deep RF analysis.
- Anomaly detection: Real-time comparison of constellation signatures (GPS, Galileo, GLONASS, BeiDou) against trusted baselines. ML algorithms identify deviations in power levels, Doppler shift, and PRN codes.
- Anti-spoofing and failover: Upon attack detection (e.g., meaconing or carry-off), the channel is isolated and the system transitions to Dead Reckoning (inertial navigation via gyros/accelerometers) or backup sources (eLoran with cryptographic protection). Alerts are sent to AI Anomaly Detection to automate response and trigger autopilot Safe Mode.
- Quantum-resistant timing: Atomic clocks (Cs/Rb) for independent synchronization resilient to GPS-time attacks—critical for AIS and VDR.
2. Hardening the ECDIS, Radar & ARPA Ecosystem (Endpoint Hardening)
Navigation equipment running legacy operating systems (e.g., Windows Embedded) is protected through an isolation-and-compensation strategy while preserving IMO certification (Type Approval).
- USB Decontamination Kiosks (Sanitization Stations): A physical barrier for removable media (ENC charts, updates). Multi-layer scanning: AV engines with ML for zero-day threats, cryptographic signature verification, and sandbox testing. Transfer into the RED ZONE only via an air-gapped interface.
- Application Whitelisting & Kernel-Level Protection: Strict execution control—only OEM-signed code (with TPM). EDR monitors system calls to prevent malware and ransomware.
- Radar-specific hardening: AI-based echo analysis to detect synthetic targets produced by EW (electronic warfare) attacks, correlated with GNSS Firewall outputs to validate positions.
3. Deep Protocol Inspection & Segmentation
NMEA (0183/2000) protocols are a potential attack vector due to the lack of authentication. The IDS/ISM stack is extended for navigation-specific traffic.
- NMEA Guards: Proxy filters for semantic PGN analysis. Blocking anomalous commands (e.g., unauthorized course changes) with contextual awareness (speed, weather). Behavioral ML on historical data to trigger alerts.
- Data Diode & micro-segmentation: Unidirectional data flow from the RED ZONE to other zones via an optical diode. SDN isolates subsystems, preventing attacker lateral movement.
- Advanced threat hunting: Regular firmware scanning for backdoors and memory forensics using tools such as Volatility.
4. Software-Based Safeguards Against Unauthorized Access
Focuses on preventing access to computing infrastructure (servers, databases, OT devices) through Least Privilege and Defense-in-Depth software controls.
- RBAC with ABAC: Dynamic roles (e.g., “Navigator” — access limited to ECDIS) enriched with attributes (time, vessel status). A centralized IdP (SAML/OAuth) integrates with Active Directory.
- MFA & SSO: Mandatory multi-factor authentication for interfaces (e.g., YubiKey tokens). SSO with session revocation upon anomalies.
- Encryption at rest/in transit: AES-256 plus post-quantum cryptography for data (e.g., VDR repositories). Keys stored in HSM Quantum Core with 90-day rotation. TLS 1.3 for traffic.
- WAF & EDR: Protection against injections/XSS in management panels; endpoint process quarantine.
- SIEM integration: Immutable event logs with alerts for brute-force and privilege escalation.
5. Specialized Audit: “Cyber-Sea Trials”
Non-intrusive assurance testing to validate controls without any risk of loss of control.
- RF analysis: Spoofing/jamming emulation in a shielded environment; validation of response and failover.
- Bridge Segmentation Verification: Detection of hidden inter-zone connectivity (VLAN hopping).
- ECDIS Integrity Check: Forensic compromise assessment and hash verification of ENC.
- Human-factor simulation: VR-based crew training for attack scenarios to assess resilience.
- Software validation: Simulated attacks against RBAC/MFA, vulnerability analysis (SAST/DAST), alignment with IMO MSC.232(82).
Integration with the overall architecture
- With the Active Monitoring section: enriches OT Cyber Sensor telemetry with navigation anomalies.
- With the Red Zone: extends “Navigation & GOT” with spectrum-level protection.
- With the overall architecture: strengthens the RF perimeter, synergizing with Zero Trust and Quantum Core.
This module not only neutralizes current threats, but also prepares for future ones such as drone swarms or quantum-era attacks. A pilot audit is recommended to tailor controls to your specific vessel.
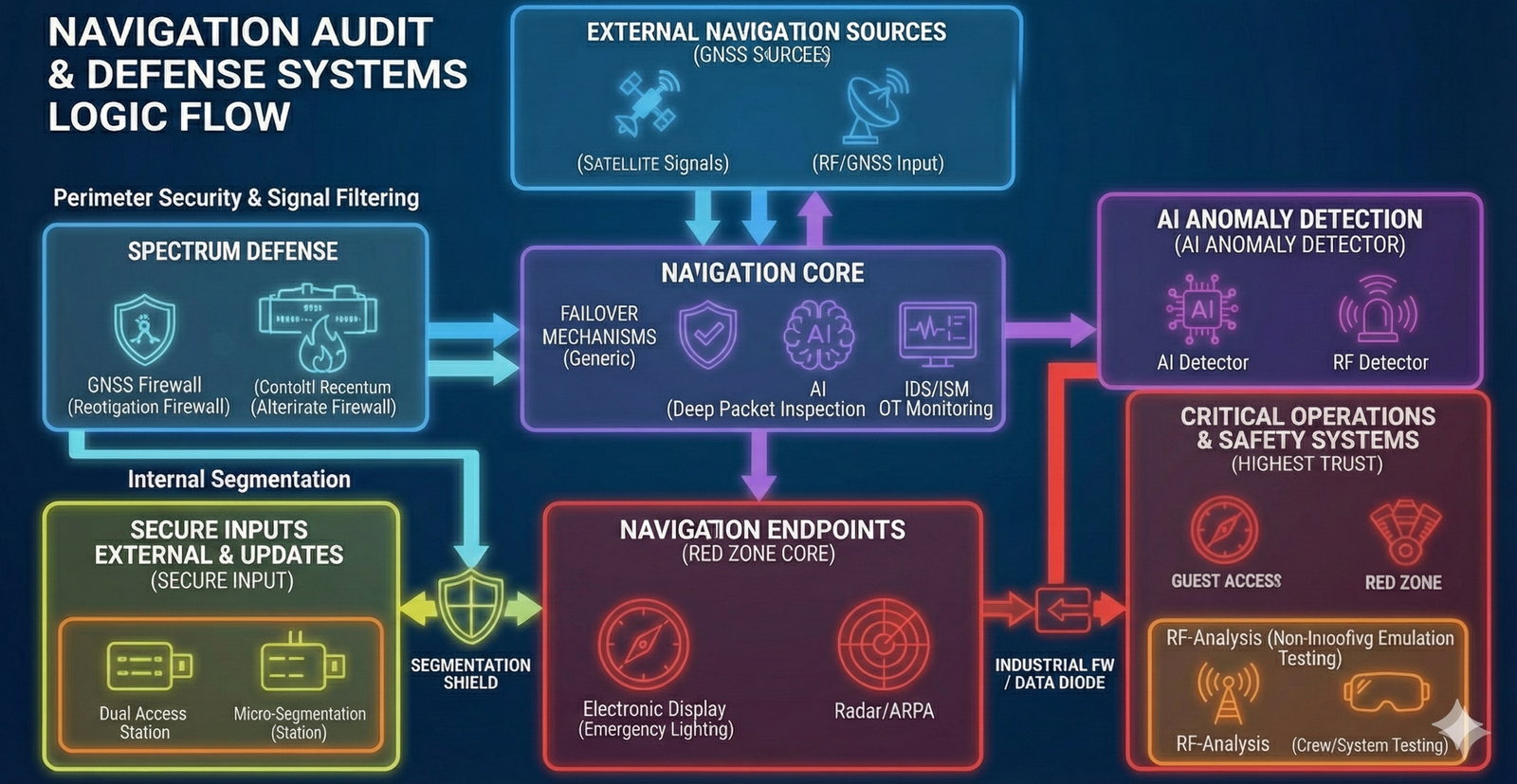
Flowchart: Operating Logic of Navigation Audit & Protection Systems
1. External Layer: Signal and Data Ingress (RF/GNSS Input)
- Components: Satellite signals GPS/Galileo/GLONASS/BeiDou, radio-frequency interfaces (RF Antennas).
- Function: Acquisition of primary positioning data and spectrum inputs for vessel navigation.
- Flow: Ingress point for all external signals.
2. Security Perimeter and Signal Filtering
- Components: CRPA antennas (Controlled Reception Pattern Antennas), GNSS Firewall (Navigation Firewall).
- Function: Physical/hardware signal filtering to detect and block spoofing/jamming; signature comparison against trusted baselines.
- Components: Inertial navigation (IMU/Dead Reckoning), alternative sources (eLoran, Quantum-Resistant Timing).
- Function: Automatic transition to autonomous modes upon attack detection.
- Feature: Isolation from external threats; alerting to AI Anomaly Detection.
3. Core Layer: Processing and Monitoring
- Components: NMEA Guards (Deep Protocol Inspection), integration with IDS/ISM OT Monitoring.
- Function: Semantic command analysis (PGN), routing data to ECDIS/radars, real-time anomaly detection.
- Components: AI detector, cyber sensors in the Red Zone, alert dashboards.
- Function: The “brain” of protection. Ingests data (logs/anomalies) from the perimeter and endpoints for real-time analysis; integration with a Data Diode for unidirectional telemetry export.
4. Internal Segmentation: Endpoint and Interface Protection
Ingress control: Application Whitelisting / Kernel-Level Protection.
TRACK A: Navigation endpoints (Red Zone Core)
- Systems: ECDIS (Electronic Chart Display), radars (X/S-band), ARPA.
- Status: Legacy OS isolation, blocking of unauthorized code, EDR monitoring.
TRACK B: Removable media and updates (Secure Input)
- Systems: Physical gateway for ENC charts and firmware packages.
- Mechanism: Multi-layer scanning (AV/ML, cryptographic verification).
- Systems: SDN to isolate subsystems and prevent lateral movement.
5. Critical Infrastructure: Audit and Verification (Audit Layer)
TRACK C: “Audit” zone (Non-Intrusive Testing)
Critical barrier: Shielded environments / Simulators (Isolated Test Environments).
Principle: Non-intrusive methods that eliminate the risk of loss of control. Audit data is exported for analysis but does not affect live systems.
- Systems: RF analysis (spoofing emulation), Bridge Segmentation Verification, ECDIS Integrity Check.
- Status: Full compromise assessment.
- Systems: VR attack simulations, Memory Forensics (Volatility).
- Function: Testing crew and system response; alignment with IMO/SOLAS compliance objectives.
