Satellite Communications Protection
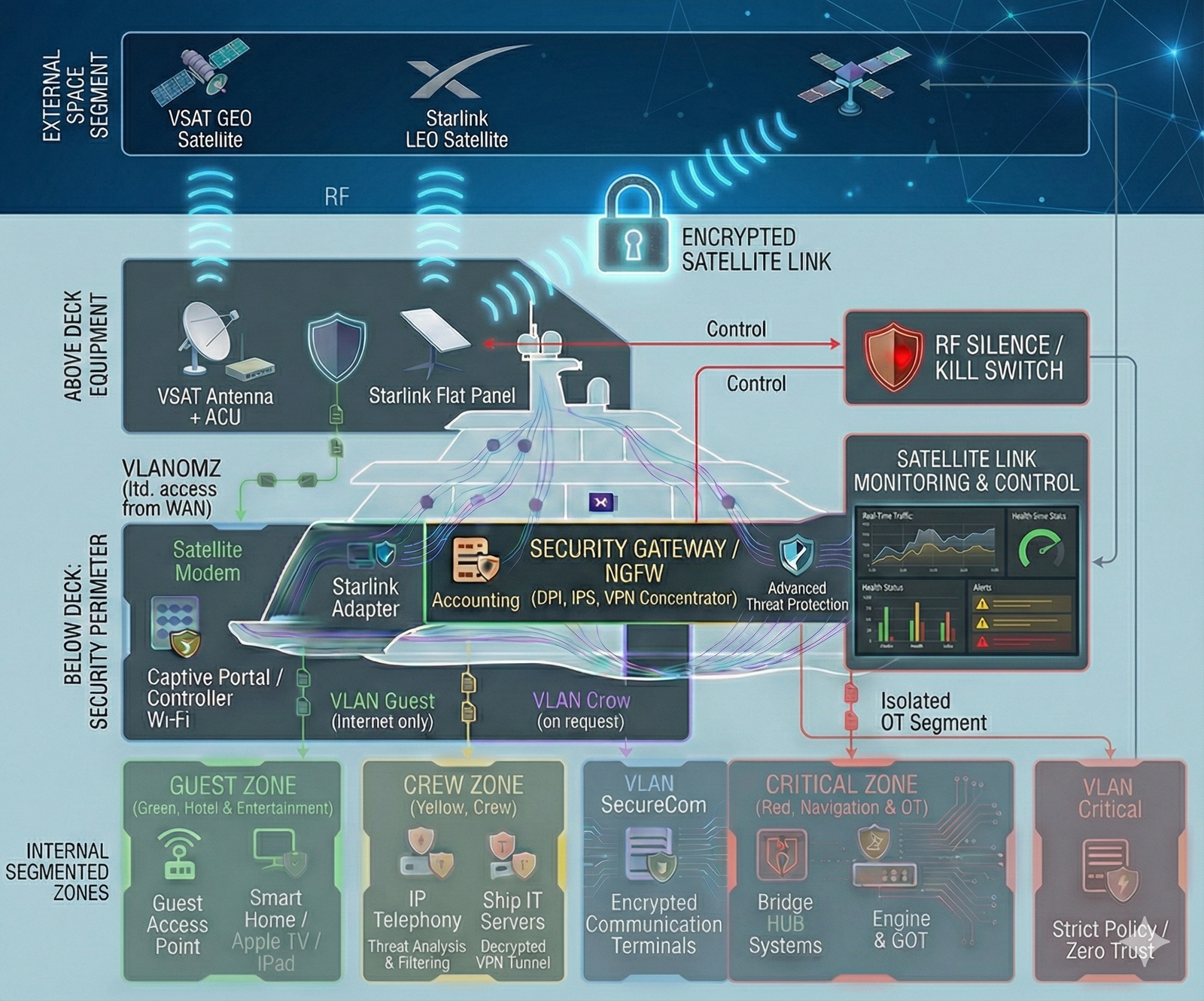
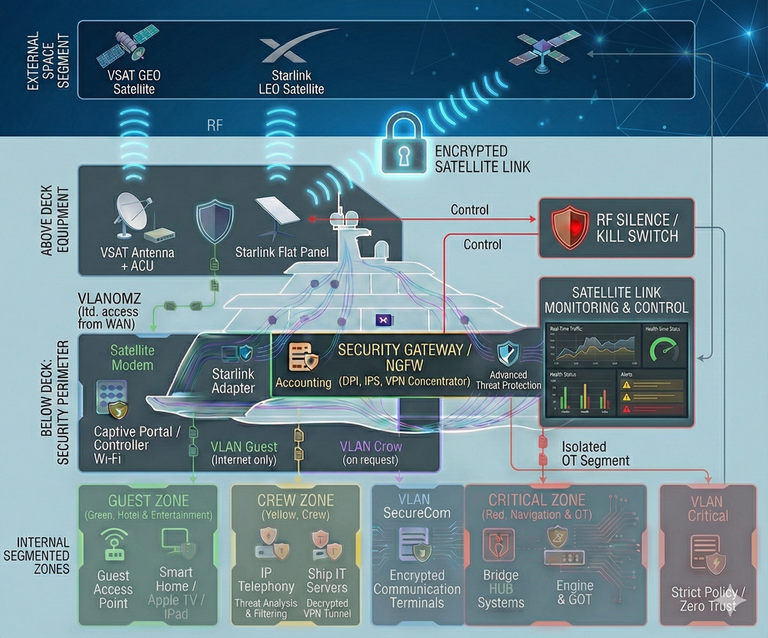
Solution Architecture: Layered Protection for Satellite Communications
The solution is designed around the principle of Defense-in-Depth, where the satellite link is treated as an untrusted external environment (Untrusted WAN). The security architecture is deployed inline between the satellite equipment and the yacht’s local network.
Key architectural components
- Satellite Link Termination: The incoming signal from the BDE (Below Deck Equipment — VSAT satellite modems or Starlink terminals) is not allowed to enter the network directly. The first ingress point is a dedicated Edge Security Gateway (Security Gateway / NGFW). This is the “fortress wall” that separates external RF equipment from the internal digital environment.
- Cryptographic Gateway (VPN Concentrator): All operational and mission-critical traffic (shore office connectivity, telemetry, vendor access) is encapsulated into protected VPN tunnels (IPsec/SSL) using modern cryptographic suites. Tunnel termination and decryption occur exclusively on the controlled onboard gateway—not on the user’s endpoint—mitigating Man-in-the-Middle attacks over the radio link.
- Segmented Routing: After gateway inspection, traffic is strictly routed only into its corresponding isolated network segment (VLAN). “Dirty” public Internet traffic from Starlink is delivered only to the Guest zone, while a secured VSAT channel may be permitted access to the crew operational zone. Direct access from any satellite link into the Critical zone (OT/Navigation) is physically and logically blocked.
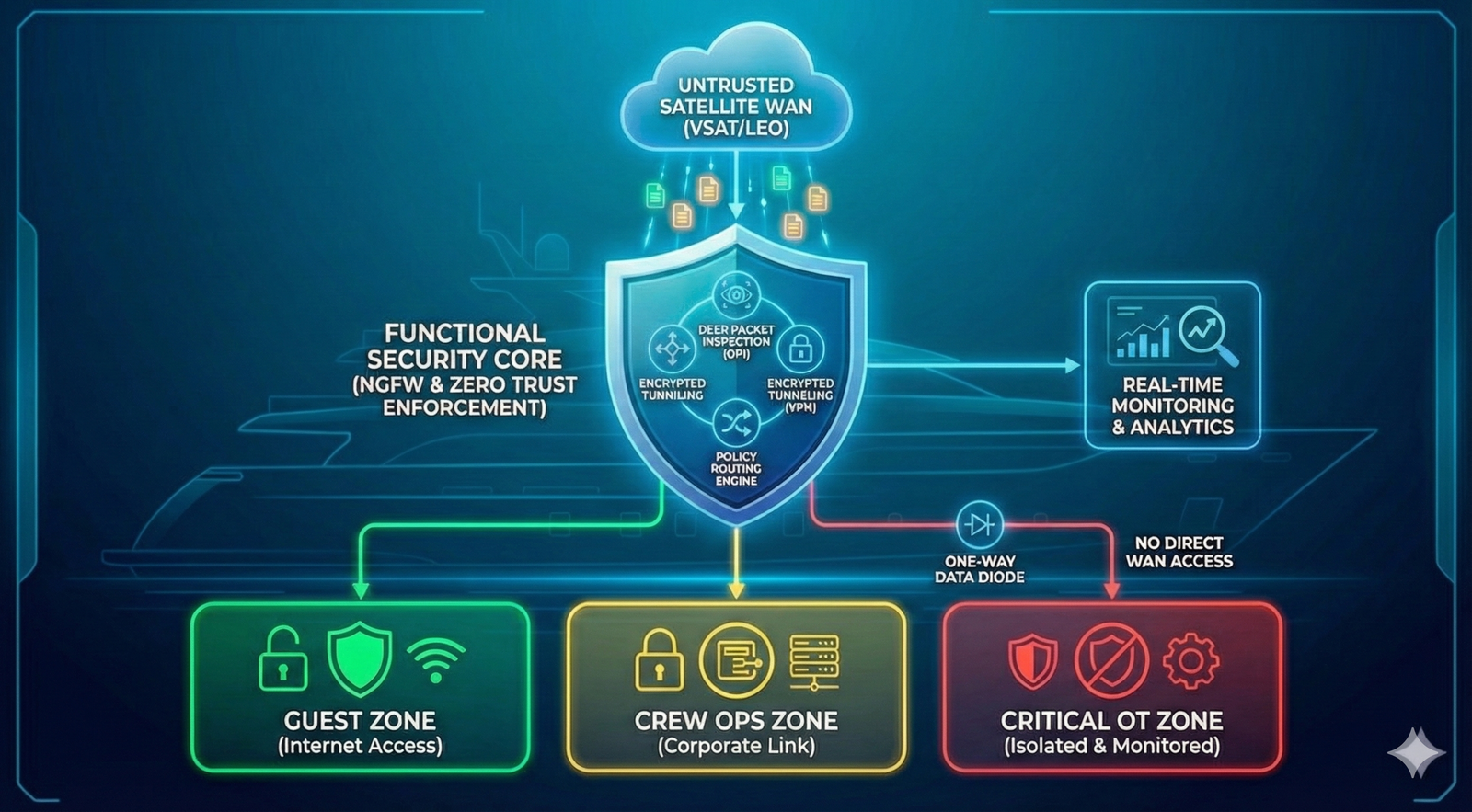
Functional Architecture: Secure Satellite Gateway
The presented architecture describes the operating model of the Secure Satellite Integration system. The solution provides secure aggregation of satellite communication channels (VSAT/LEO) and their logical sterilization prior to delivery into the vessel’s internal network, enforcing a Zero Trust principle toward all external communication links.
1. External Segment & Emission Control (RF Layer)
At the physical layer, the system manages interaction with the space segment, treating the radio spectrum as a potentially hostile environment.
- Multi-Orbit Aggregation: Concurrent operation with geostationary (VSAT GEO) and low Earth orbit (Starlink LEO) satellites ensures link redundancy and dynamic load balancing.
- RF Silence / Kill Switch (Radio Silence Circuit): A dedicated hardware module, RF Control Logic, allowing the operator to instantly de-energize antenna transmission paths. This guarantees the physical impossibility of vessel tracking via RF emissions and protects against RF-based threat targeting in critical situations.
2. Security Perimeter (Security Gateway Layer)
The central data processing node (“Below Deck Security Perimeter”), where logical traffic sanitization is performed.
- Security Gateway (NGFW): A single controlled ingress point for all satellite modems. Traffic is not routed directly but is terminated at the gateway for inspection.
- VPN Concentrator (Encryption Termination): Decryption of inbound VPN tunnels occurs at this layer, enabling inspection of protected payloads for malware before delivery to end systems (mitigation of threats concealed within encrypted traffic).
- DPI & IPS (Deep Packet Inspection): The intrusion prevention system analyzes packet headers and payloads, blocking exploit attempts and botnet command-and-control activity at an early stage.
3. Segmentation & Distribution (Internal Zones Layer)
After sanitization, traffic is strictly distributed across isolated virtual networks (VLANs) in accordance with defined security policies.
- GUEST ZONE (Green Zone): Provides guests with Internet and multimedia access. Traffic is fully isolated from vessel control and operational systems.
- CREW ZONE (Yellow Zone): Operational network for crew activities. Access to corporate resources is provided through authenticated and trusted VPN tunnels.
- CRITICAL ZONE (Red Zone): Navigation and OT (Operational Technology) segment. Internet access is blocked or strictly limited through whitelisting, eliminating the risk of remote takeover of vessel control systems.