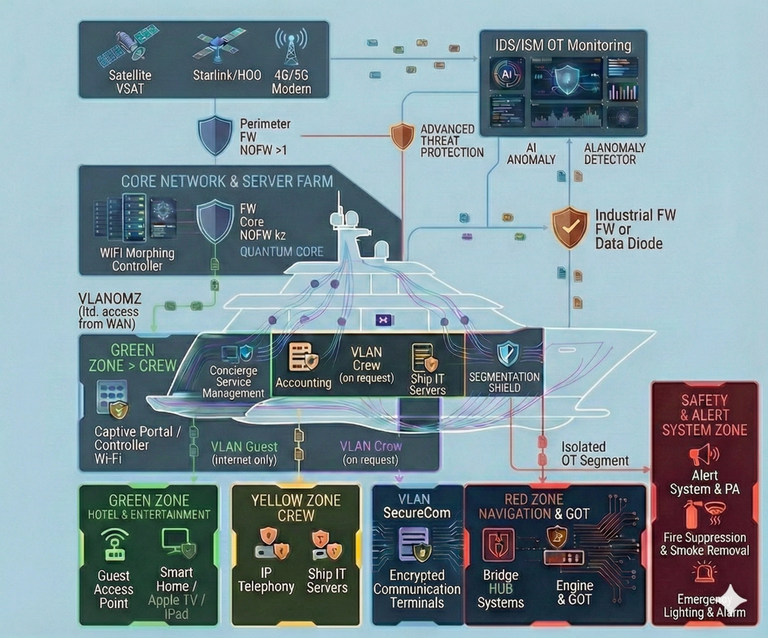
Network Architecture
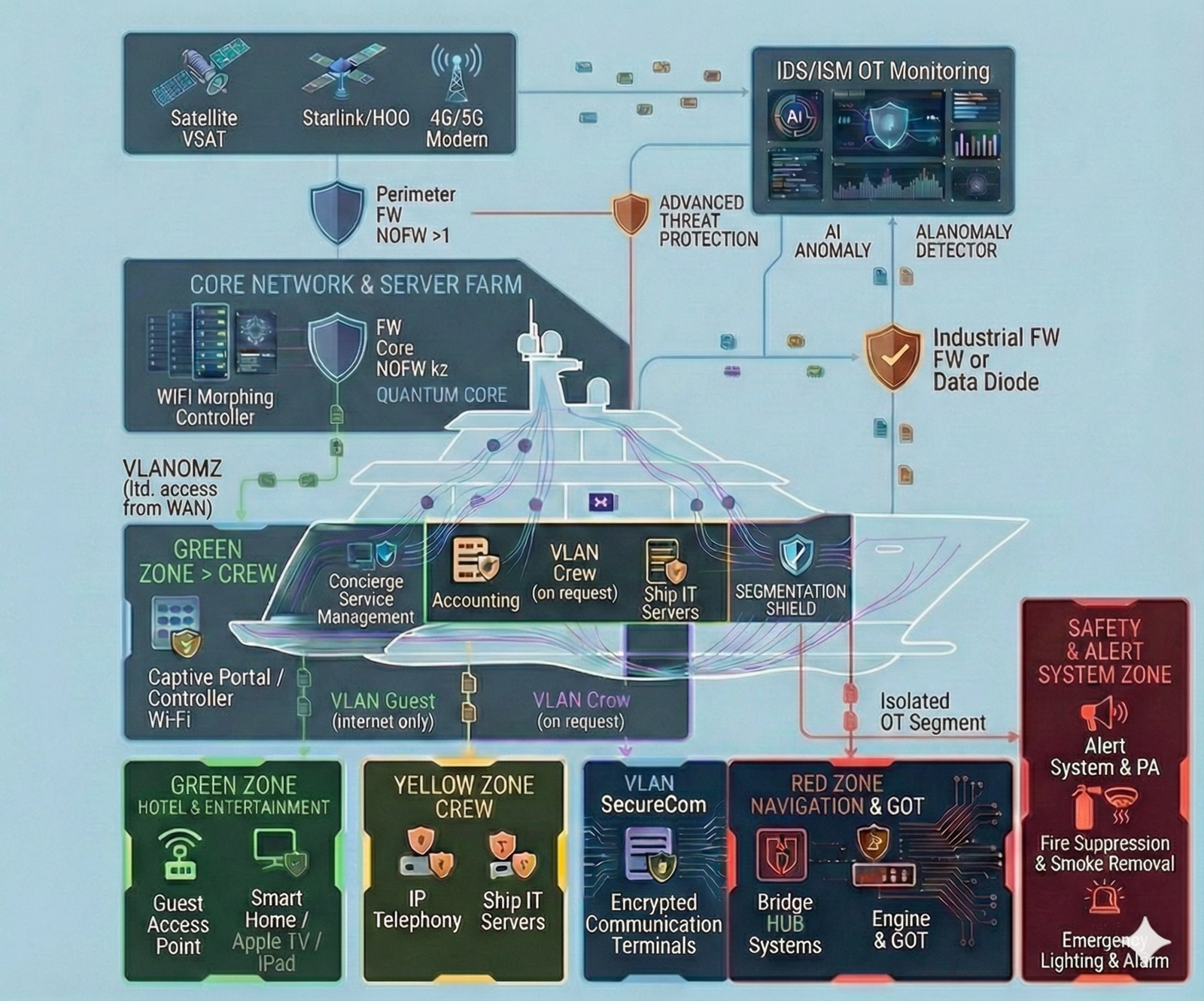
Next-Generation Yacht Cybersecurity Architecture: Technical Description
Concept Overview
The diagram illustrates an advanced cybersecurity architecture for a superyacht, built on the principles of Defense-in-Depth and Zero Trust. The solution is designed for secure convergence (integration) of guest and crew IT services with critical operational technologies (OT/GOT) used for vessel control.
The architecture leverages innovative technologies such as “Wi-Fi Morphing” and the “Quantum Core” security processing engine, as well as a multi-layer AI-driven monitoring system to counter the most modern threats.
Below is a detailed description of the protection layers and diagram components.
1. External Perimeter and Multimodal Connectivity
The first line of defense, providing flexible and secure vessel connectivity to global networks.
- Connectivity Sources: Channel aggregation to ensure connectivity anywhere in the world:
- Satellite VSAT: Traditional reliable connectivity via geostationary satellites.
- Starlink/LEO: High-speed, low-latency connectivity via low-Earth-orbit constellations.
- 4G/5G Modem: Cellular connectivity in coastal areas.
- Perimeter Firewall (Firewall) NOFW >1: A high-performance border security gateway in a high-availability configuration (>1). Performs primary traffic filtering at the “vessel–shore” boundary and terminates VPN tunnels.
- Advanced Threat Defense: A cloud or on-prem “sandbox” service for analyzing suspicious files for zero-day threats before they enter the network.
2. Protected Network Core and Services (Core Network & Server Farm)
The central node for data processing and enforcement of security policies.
- Core Firewall (FW Core) NOFW k2 "Quantum Core": The heart of the security system. A resilient internal firewall cluster (k2 configuration). The "Quantum Core" technology provides ultra-high performance deep packet inspection (DPI) and is ready for future adoption of post-quantum encryption algorithms.
- Wi-Fi Morphing Controller (Controller WIFI Morphing): An innovative wireless network management system. Uses Moving Target Defense by dynamically changing network parameters (BSSID, SSID, keys), making the Wi-Fi network “invisible” and resistant to scanning and “evil twin” attacks.
- VLANOMZ: A specialized isolated management zone for infrastructure servers, with strictly limited access from the external network (WAN).
3. Active Monitoring and AI Analytics (Overlay Security)
A security overlay for proactive real-time threat detection without interfering with system operations.
- IDS/ISM OT Monitoring: A comprehensive intrusion detection system adapted to the maritime context (ISM - International Safety Management).
- OT Cyber Sensor: Passive sensors connected to industrial networks that analyze specialized maritime protocols for anomalous commands.
- AI Anomaly Detection: An AI-based system that analyzes behavioral patterns in the network to identify hidden threats that traditional signature-based methods cannot detect.
4. Strategic Segmentation (Segmentation Shield)
The visualized “Segmentation Shield” demonstrates strict separation of the network into isolated zones with different trust levels.
- GREEN ZONE:
- Hospitality & Entertainment: An isolated segment for guests (Smart Home, Apple TV, personal devices) with Internet-only access via Captive Portal / Wi-Fi Controller.
- CREW: Segments for administrative tasks (Accounting, Concierge services) and crew personal access (VLAN Crew on request).
- YELLOW ZONE CREW: A working environment for service IT servers and IP telephony.
- VLAN SecureCom: A dedicated segment for encrypted confidential communications terminals.
5. Critical Infrastructure Protection (RED ZONE)
The “Red Zone” is a zero-trust segment hosting the vessel’s life-critical systems.
- Navigation & GOT (Navigation & GOT): Includes bridge systems (Bridge NAV Systems), engine control, and other operational technologies (Engine & GOT).
- Industrial Firewall or Data Diode (Industrial Firewall or Data Diode): A mission-critical barrier providing one-way data flow. It allows telemetry to be transmitted from the isolated OT segment to monitoring systems, while physically blocking any inbound connections or attacks into the red zone.
Glossary: Terms and Acronyms
To ensure unambiguous understanding of the advanced technologies used in this architecture, the following definitions are provided:
| Term / Acronym | Description |
|---|---|
| AI Anomaly Detection | AI Anomaly Detection. An artificial intelligence / machine learning system that identifies threats not by known-virus databases, but by deviations from normal network and user behavior. |
| Captive Portal | An authentication web page a user sees before gaining access to a public Wi-Fi network (e.g., in the guest zone). |
| Data Diode | Data Diode. A hardware cybersecurity device that physically guarantees one-way data transfer (from the protected segment outward), eliminating inbound attacks. |
| GOT | Generic Operational Technology. An umbrella term for onboard control and automation systems (engines, power, HVAC, etc.) that are critical to yacht operations. |
| IDS/ISM | Intrusion Detection System / International Safety Management. An intrusion detection system integrated with the vessel’s safety management processes. |
| LEO / НОО | Low Earth Orbit. Satellite systems such as Starlink that provide high speed and low latency. |
| NOFW (>1 / k2) | Internal notation for high-availability and high-performance Network Firewall cluster configurations. |
| OT Cyber Sensor | OT Cyber Sensor. A specialized device for passive monitoring of industrial (OT) networks without impacting technological processes. |
| Quantum Core | Quantum Core. A marketing name for a high-performance core firewall processing module designed to handle large data volumes and support future encryption methods. |
| Segmentation Shield | Segmentation Shield. A visual representation of deep logical isolation between network zones to prevent threat propagation. |
| VLANOMZ | VLAN Operations Management Zone. An isolated virtual network for infrastructure management, with access strictly limited from external networks (WAN). |
| VSAT | Very Small Aperture Terminal. Traditional satellite communications via geostationary satellites, providing global coverage. |
| WIFI Морфинг | WiFi Morphing. A Moving Target Defense technique for wireless networks. The controller continuously changes network parameters (BSSID, keys, etc.) to prevent reconnaissance and Wi-Fi attacks. |
| FW | Firewall. |
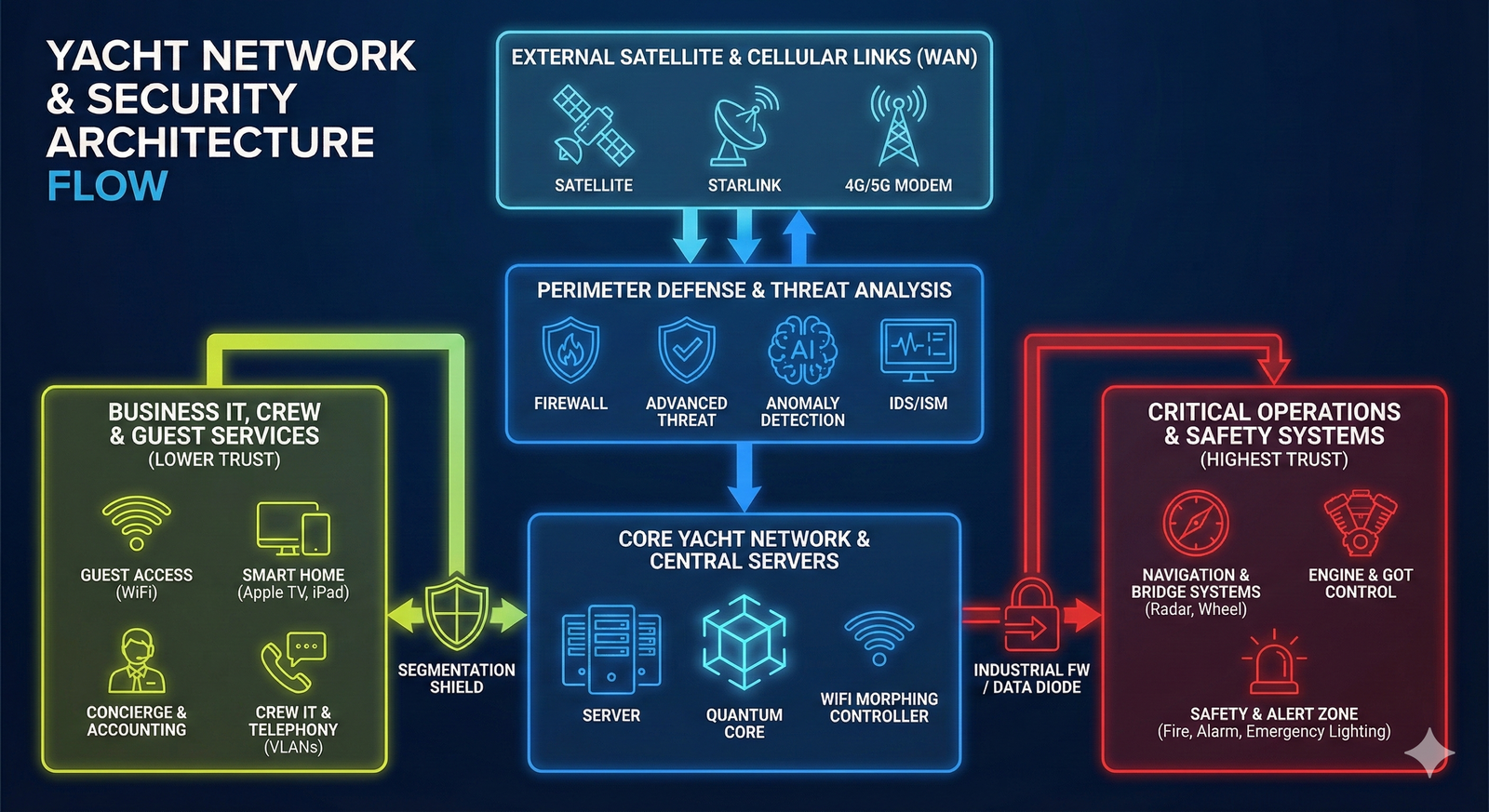
Block diagram of yacht systems logic
1. External layer: Connectivity and Data Ingress (WAN)
BLOCK: External connectivity channels (WAN Sources)
- Components: Satellite VSAT, Starlink/HOO, 4G/5G modems.
- Function: Provides global connectivity and Internet access.
- Flow: Entry point for all data.
2. Security perimeter and Access Control
BLOCK: Perimeter protection
- Components: Perimeter firewall (Perimeter FW), Advanced Threat Protection.
- Function: “Allow/deny” traffic filtering, blocking external attacks.
BLOCK: Special access (VLAN OMZ)
- Components: VLAN OMZ (Operations Management Zone).
- Function: A restricted-access zone reachable from the WAN. Used for remote administration or technical support.
- Note: An isolated channel that does not mix with guest or general traffic.
3. Core layer: Network intelligence
BLOCK: Network core and server farm
- Components: Quantum Core, Core Firewall (FW Core), Morphing Wi-Fi Controller.
- Function: Traffic routing, seamless roaming management (Wi-Fi), resource allocation.
BLOCK: Global security monitoring (IDS/ISM OT Monitoring)
- Components: AI anomaly detector, cyber sensors, monitoring dashboards.
- Function: The security “brain.” Receives data (logs/alerts) from the perimeter and from the isolated OT segment (via a data diode) to analyze the vessel’s status in real time.
4. Internal segmentation: User and Service zones
STREAM A: Guests and Entertainment (Green zone)
Ingress control: Captive Portal / Wi-Fi Controller (user authentication).
- BLOCK: Hospitality and Entertainment
- Systems: Guest access node, Smart Home, Apple TV / iPad.
- Status: Fully isolated from vessel control systems. Internet only.
STREAM B: Crew and Administration (Green/Yellow zones)
- BLOCK: Crew Services (Green Zone > Crew)
- Systems: Concierge service management, Accounting.
- Systems: Onboard IT Servers (On request) — servers available by request only.
- BLOCK: Crew Operations (Yellow Zone)
- Systems: IP telephony, shared crew servers.
- BLOCK: VLAN SecureCom
- Systems: Encrypted communications terminals (confidential discussions).
5. Critical infrastructure: OT and Safety (Red zone)
STREAM C: “Red” zone (maximum protection)
Critical barrier: Industrial firewall or Data Diode.
Principle: One-way data flow. Information may exit for monitoring, but nothing from outside can enter.
BLOCK: Navigation and Control (Red Zone)
- Systems: Bridge hub systems (Bridge HUB Systems), Engine and GOT systems.
- Status: Full isolation.
BLOCK: Life-Safety Systems (Safety & Alert System Zone)
- Systems: Public Address system (PA), Fire suppression and smoke extraction, Emergency lighting and alarms.
- Function: Autonomous vessel physical safety systems.