Commercial Proposal
Digital Vessel Technical Passport for IT/OT & Cybersecurity + AI Module for Control & Recommendations
Tailored to a specific vessel • From design to operations
The Digital Vessel Technical Passport for IT/OT & Cybersecurity
(yachts, passenger vessels — cruise ships/liners, ferries, dry cargo vessels,
tankers, etc.) is a web platform and software environment that serves as a
continuously updated single source of truth for operational management and control of onboard
digital infrastructure (IT/OT) and its cybersecurity posture — from asset inventory and configurations
to security events, vulnerabilities, and practical response recommendations.
The solution consolidates fragmented diagrams, design decisions, service reports, event logs, and configuration data into a
single managed environment, where everything is linked:
assets ↔ configurations ↔ vulnerabilities ↔ accountability ↔ procedures and playbooks.
This is especially important for vessels where infrastructure evolves over years, contractors and crews change,
and critical technical knowledge often sits across multiple sources.
Important: not an off-the-shelf product not mass-market
This is not a packaged product deployed using a generic template.
We develop the codebase, data model, and configuration specifically for your vessel,
taking into account:
- the actual architecture of onboard systems, network segments, and communication links;
- the operating model (routes, connectivity modes, shore services, contractors, remote-access domains);
- shipowner/master/shore team requirements, as well as applicable standards and internal policies;
- accountability and authority structure across onboard and shore functions;
- IT/OT interaction specifics, critical dependencies, and single points of failure.
The result is a system that reflects your real configuration (not an “average case”)
and supports practical readiness: day-to-day operations and planned maintenance — as well as incidents and inspections.
Why this matters specifically for vessels (not like “office IT”)
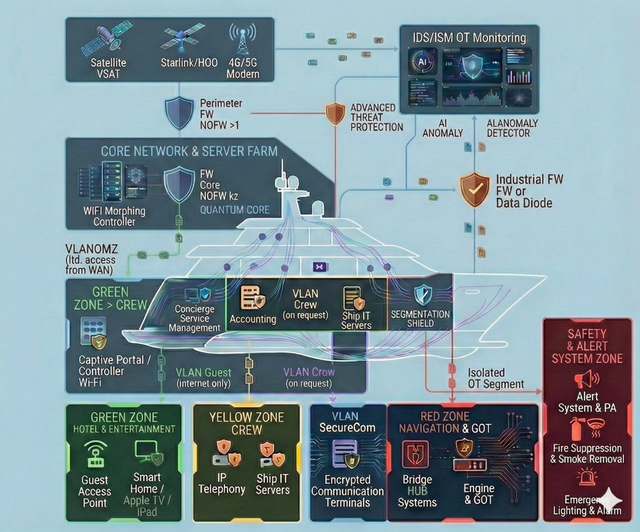
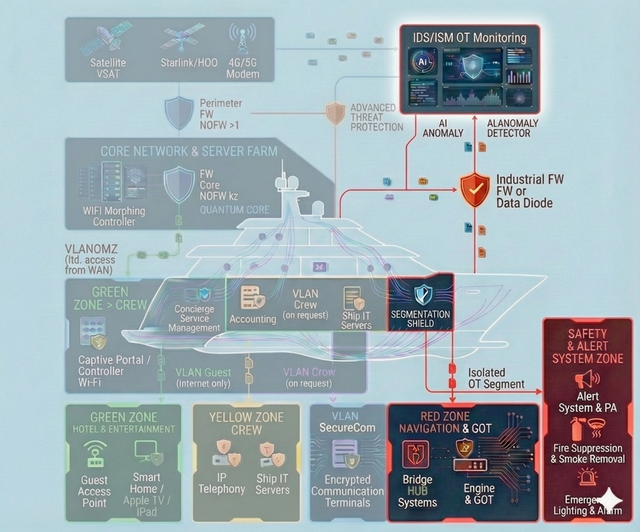
Onboard digital infrastructure has unique characteristics compared to classic corporate environments:
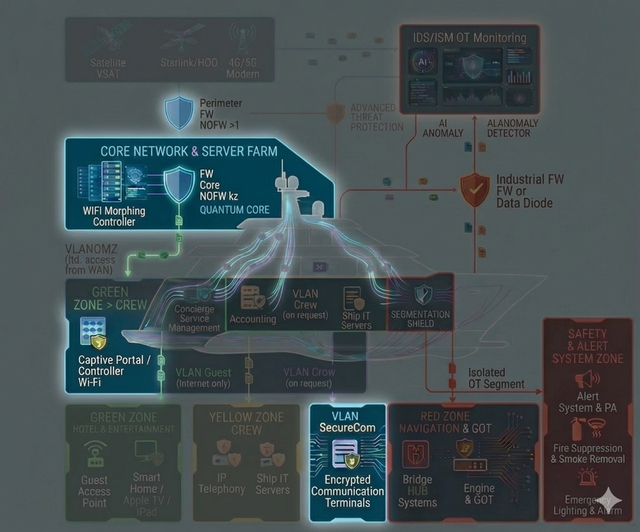
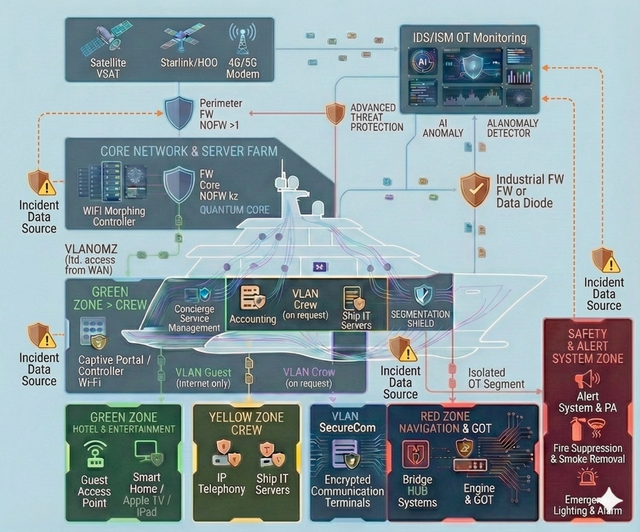
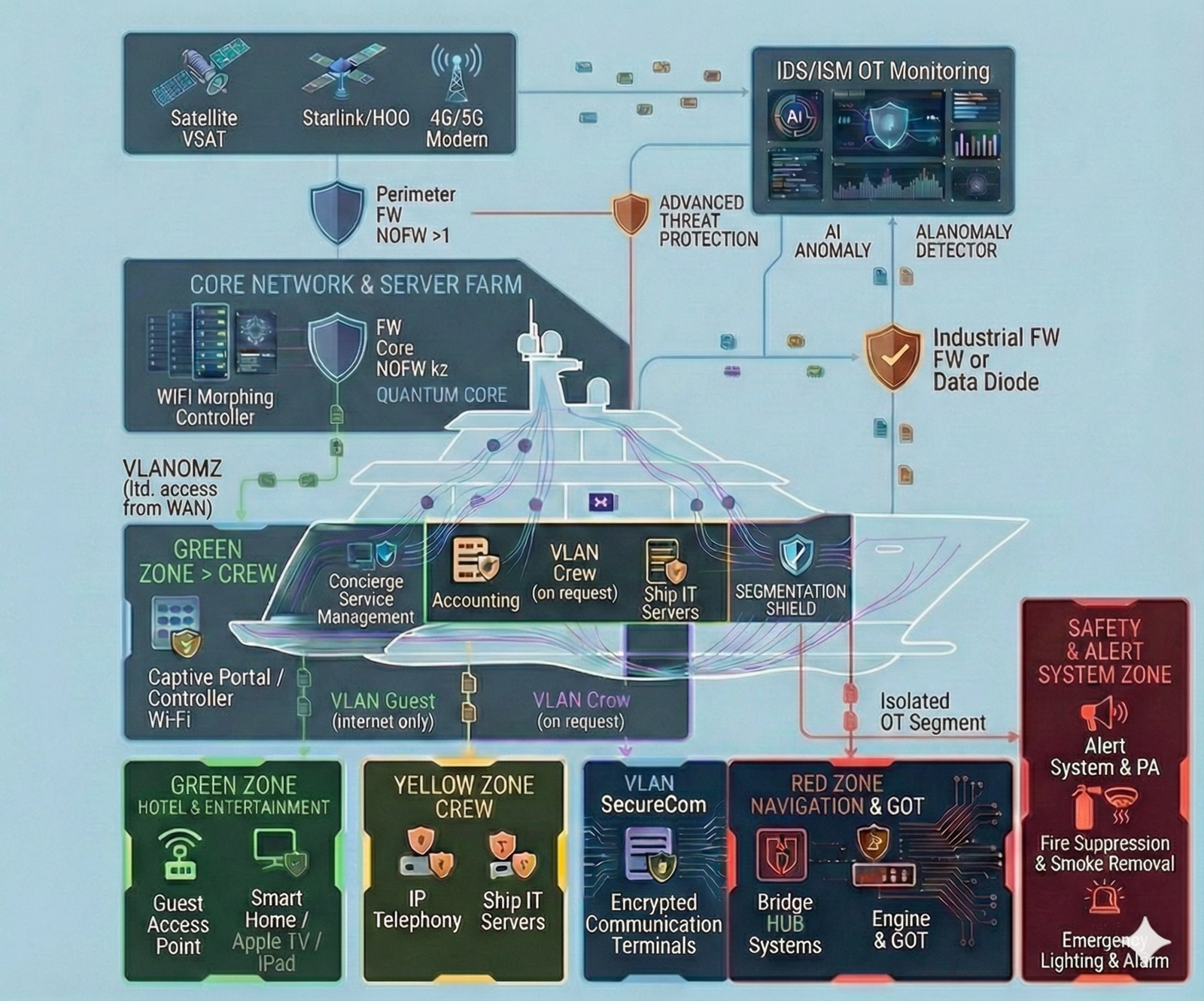
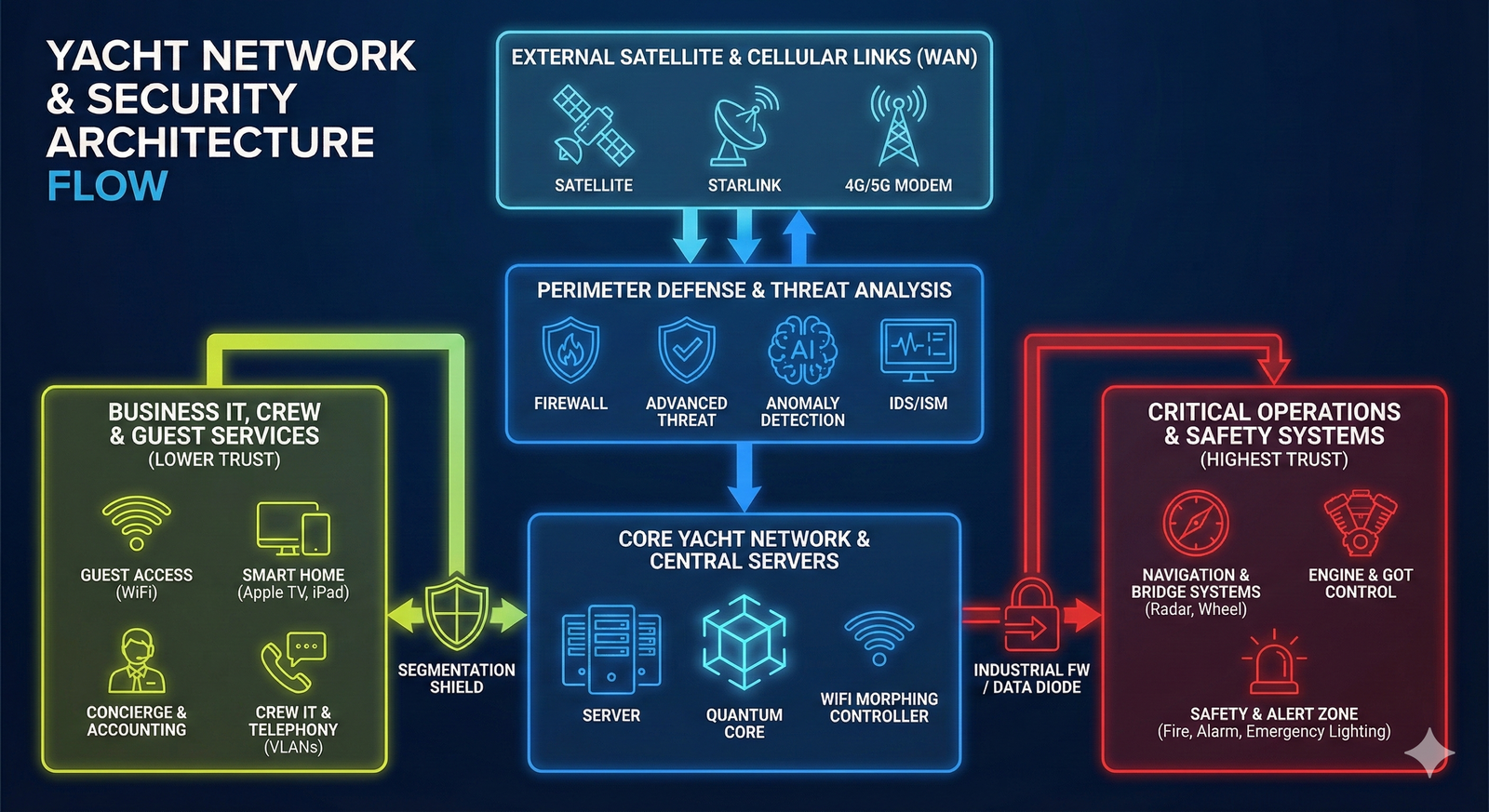
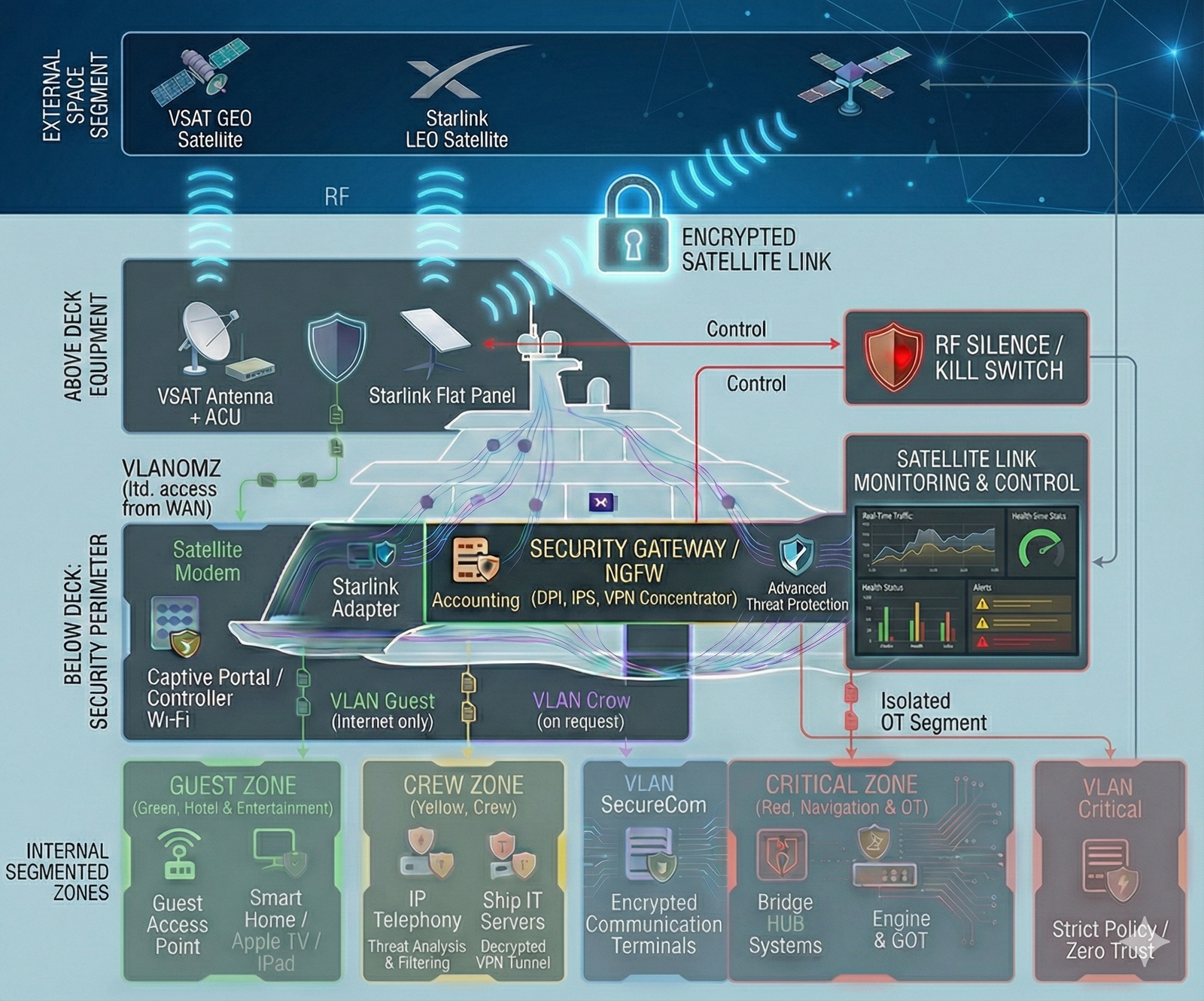
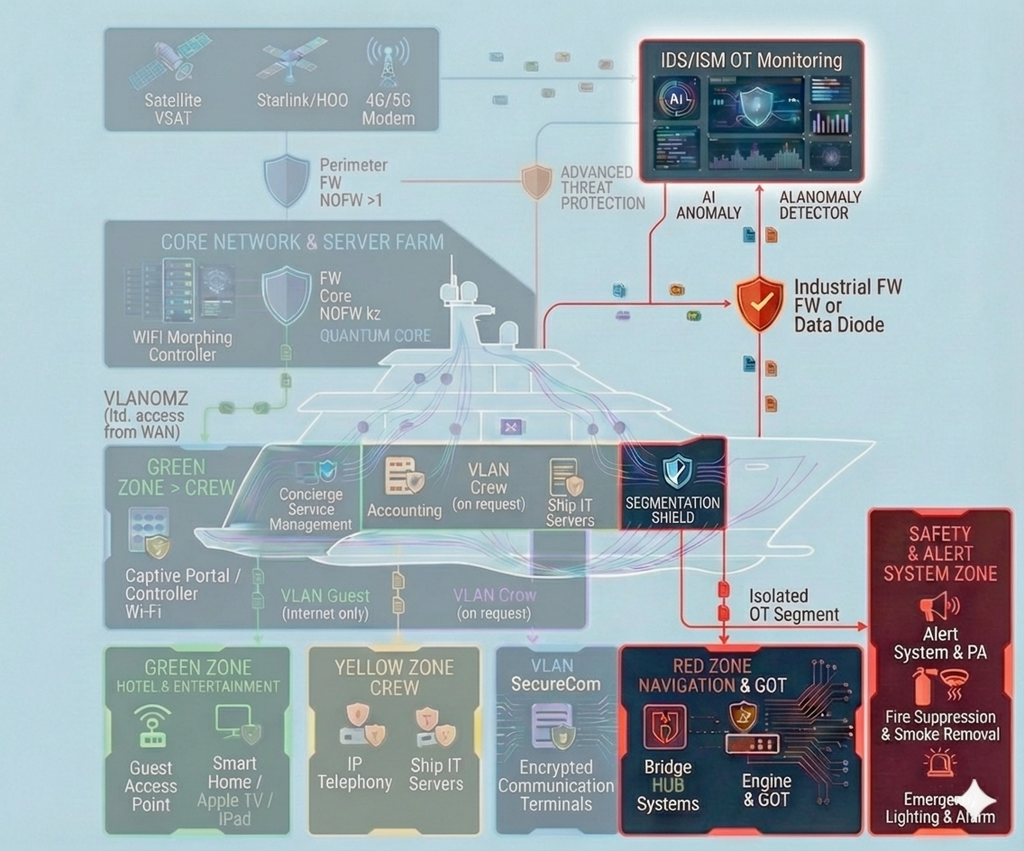
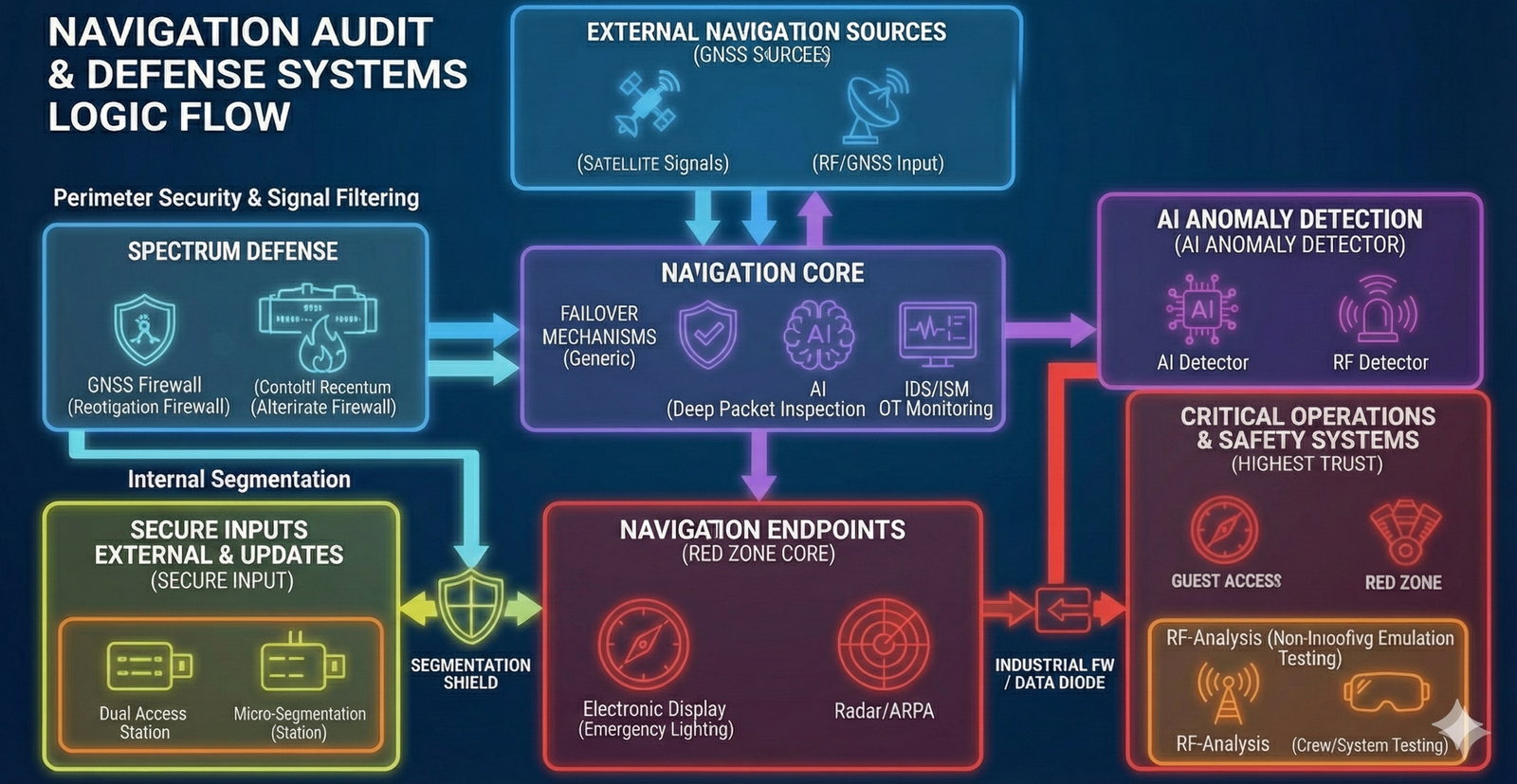
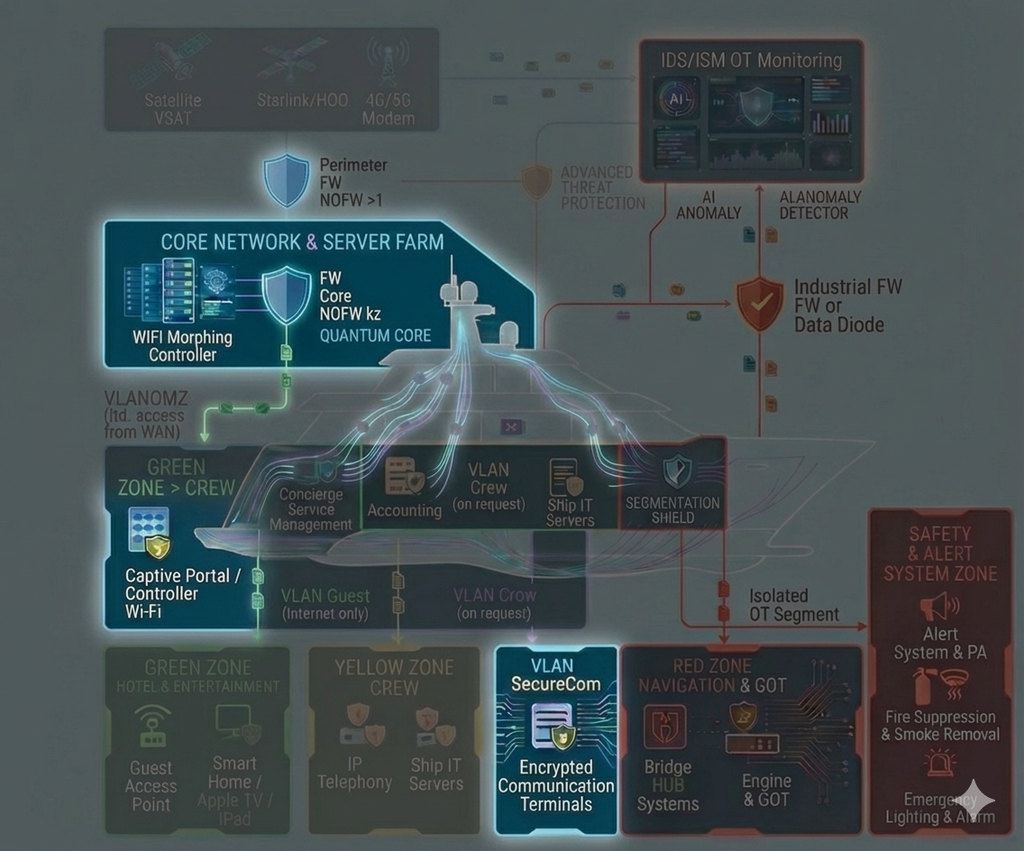
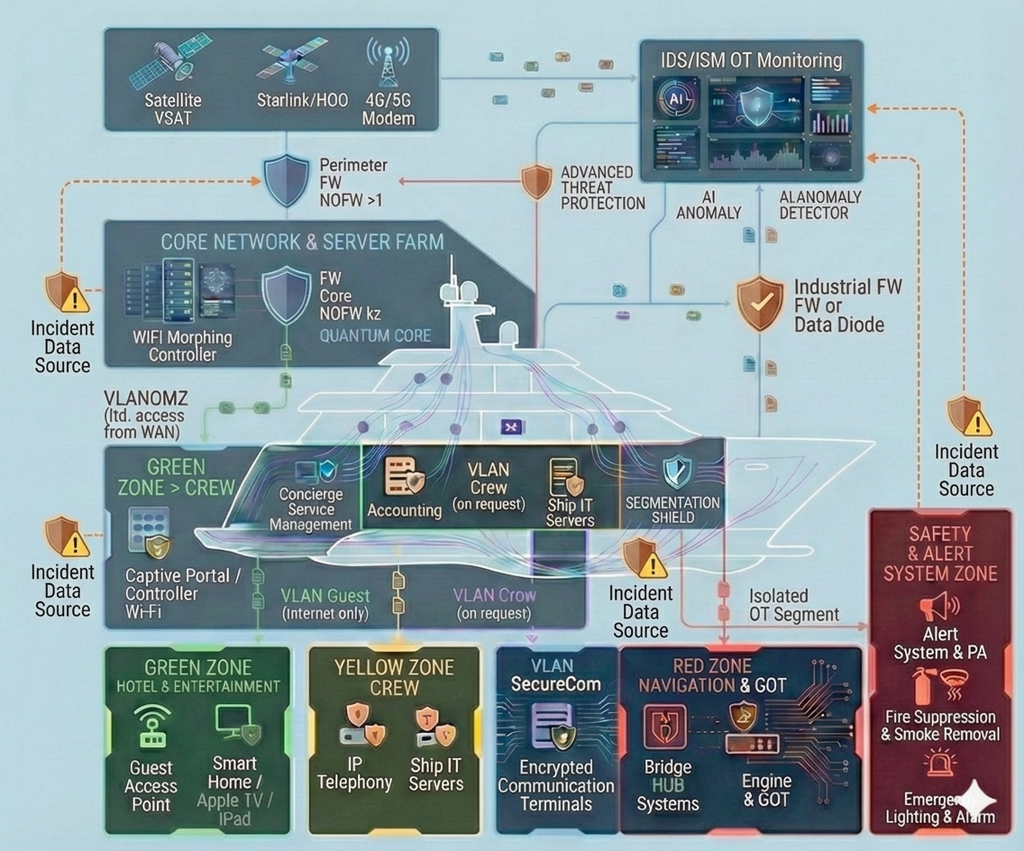
- Mixed IT/OT: navigation, communications, automation, safety systems, service subsystems and classic IT are interconnected and interdependent.
- Limited connectivity and autonomy: vessels operate with unstable and expensive links; “office-like” instant support is often unavailable.
- High cost of error: a wrong update, improper action, or failure of a critical node can cause downtime, financial losses, and safety risks.
- Long lifecycle: refits, repairs, equipment replacements and contractor turnover quickly devalue documentation unless maintained systematically.
- Continuous audit readiness: compliance is not a one-time effort — it is a sustained, provable operational state.
The Digital Technical Passport addresses these maritime realities: it captures the as-is state, keeps it current, and helps teams act correctly
even with limited connectivity and time pressure.
When we can engage (any vessel lifecycle stage)
We can start not only during operations, but also at stages where early decisions bring maximum impact and reduce future risks:
vessel design, shipyard build/commissioning,
refit, repair and recovery, and
ongoing managed support.
1) Vessel design stage
- support in shaping the target IT/OT and communications architecture;
- security-by-design: segmentation, trust zones, access principles, logging and monitoring “done right from day one”;
- requirements for vendors and contractors (documentation, access, updates, support);
- laying the foundation for the Digital Technical Passport before entry into service.
2) Shipyard build / commissioning
- normalizing and structuring documentation for the as-built configuration;
- change control: what is installed and how it is connected;
- capturing configurations and integration links before handover;
- building a living digital model instead of a static archive.
3) Refit
- assessing the security and resilience impact of changes;
- updating diagrams, data model, procedures and control domains;
- preventing “technology layering” that increases complexity and risk.
4) Repair / recovery / replacements
- quickly capturing changes and restoring a coherent picture;
- reducing the likelihood of recurring failures and incidents;
- updating the Passport and procedures, reducing reliance on “tribal knowledge”.
5) Operations and ongoing support
- keeping data current; monitoring vulnerabilities, events and changes;
- improving cybersecurity process maturity with minimal burden on the crew;
- working with onboard and shore teams / the management company.
The Digital Technical Passport becomes a lifecycle component: from concept to years of operation,
ensuring continuous visibility, evidence and control.
What you get (value for shipowners, masters and shore teams)
1) A single source of truth for infrastructure and changes
- inventory of equipment, network nodes, servers, workstations, communication and automation systems;
- tracking software, firmware, licenses, asset criticality and onboard usage zones;
- change history (who/when/what), version control and update governance;
- fast access to design and operational documentation, diagrams, settings and procedures;
- a consistent information model: knowledge stops being “spread across folders, people and contractors”.
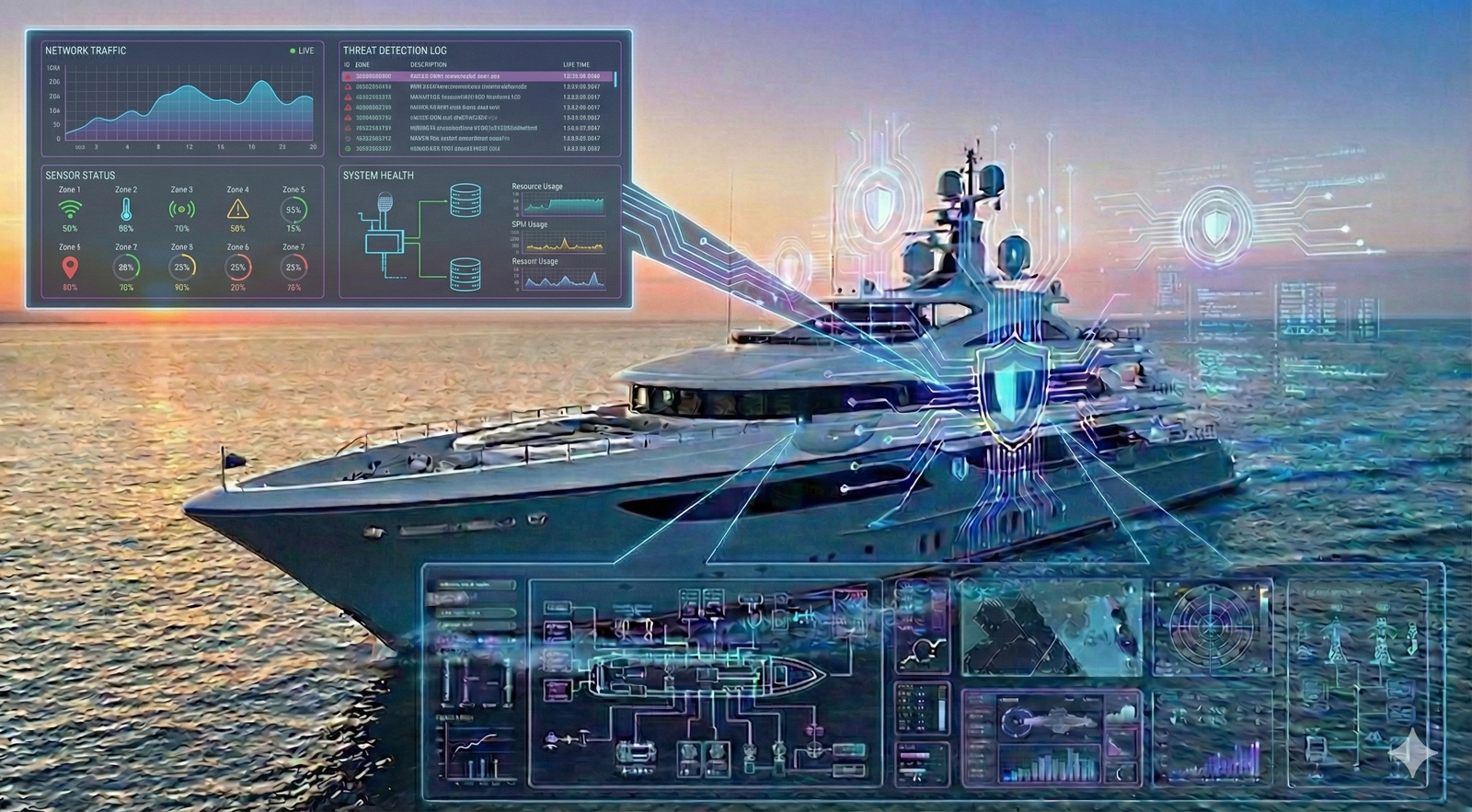
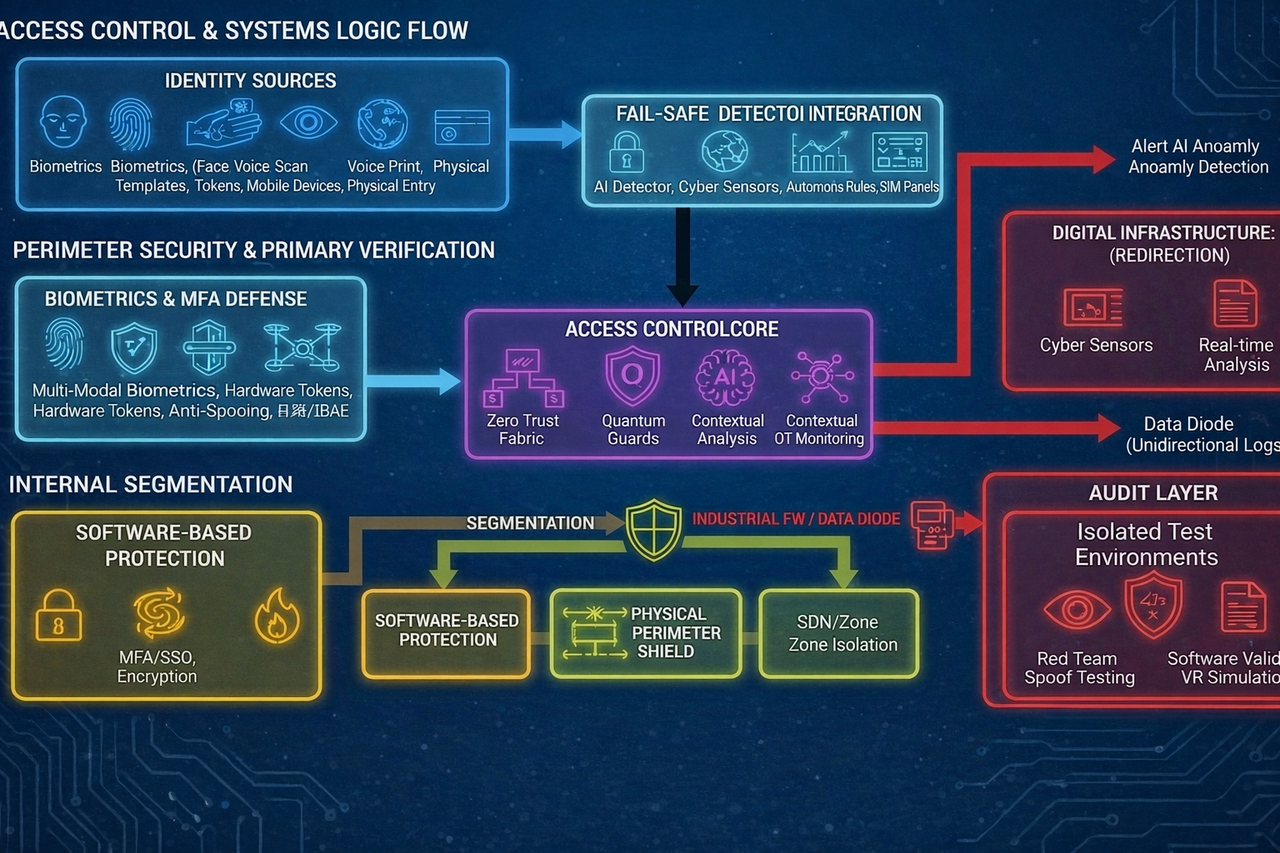
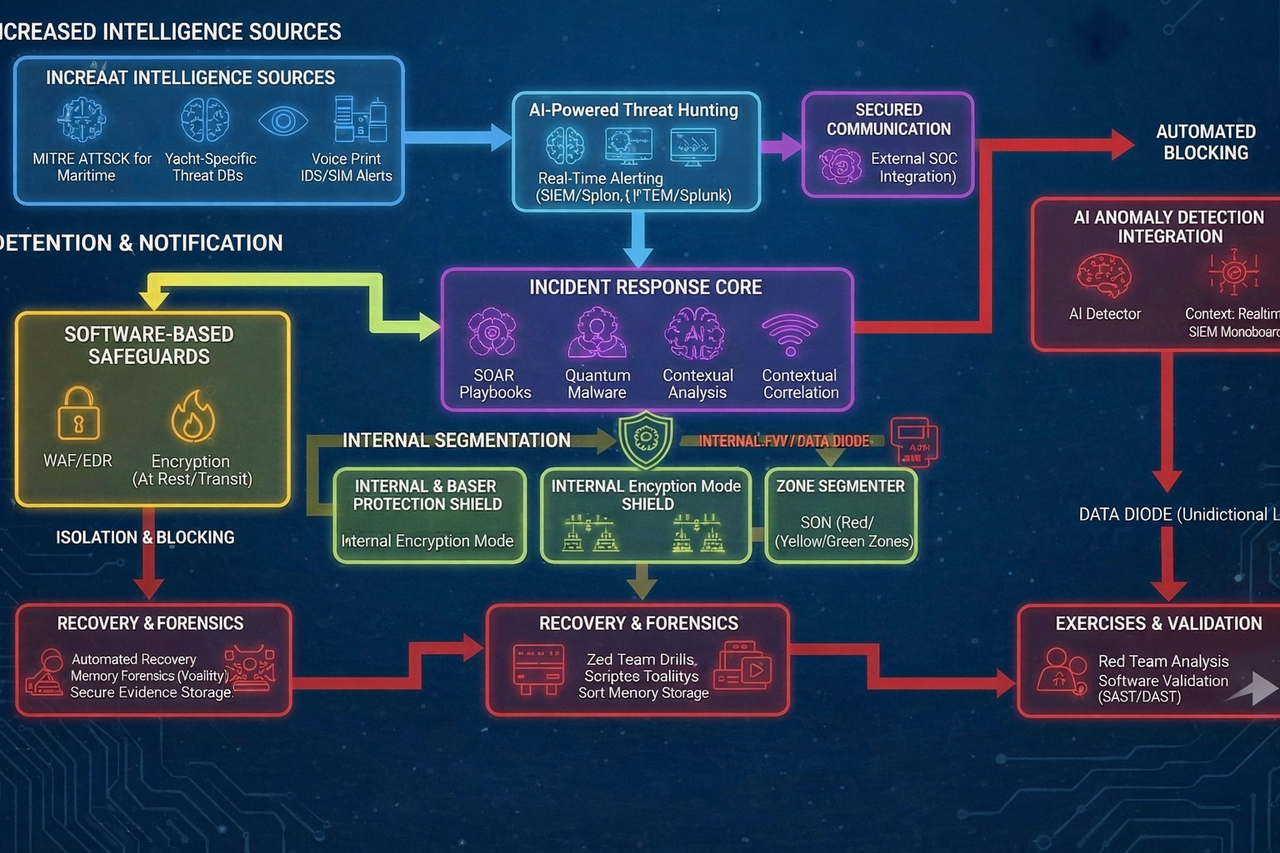
2) Intelligent alerting and recommendations (AI module)
The AI module acts as an “intelligent assistant” for the crew and shore team:
- reduces false positives and operational noise;
- prioritizes real threats and alerts only on what matters;
- provides action guidance: what to isolate, what to verify, which steps are safe;
- shortens response time and reduces downtime impact;
- supports consistent playbooks when decisions must be fast and safe.
AI is valuable not only for security, but also for operations: it accelerates diagnostics, helps identify cause-effect links between changes and failures,
and suggests safe actions under limited connectivity. If required, the AI module can operate in an architecture where data remains on the client side
(depending on the chosen deployment model and information handling policy).
3) Audit and inspection readiness without “fire drills”
- data and documentation remain up to date;
- evidence packages are produced (controls, configurations, procedures, artifacts);
- reduced dependency on individual specialists (“knowledge is in the system”);
- stronger risk governance and demonstrable compliance.
Economic impact and ROI (what you save)
Lower incident and downtime costs
- faster root-cause identification and containment (AI + structured data model);
- fewer human errors under stress (procedures and guidance are immediately available);
- reduced likelihood of repeat incidents through change governance and root-cause analysis.
Lower total cost of ownership (TCO)
- configuration and change governance reduces repeated failures;
- planned updates and replacements reduce emergency and unplanned work;
- visibility into contractors, access and accountability reduces hidden operational risks.
Reduced documentation effort
- documentation, diagrams and configurations are structured and readily accessible;
- less manual compilation before audits and fewer non-conformance risks;
- simpler handover between crews, managers and service organizations.
Note: exact ROI is refined after reviewing inputs (system scope, operating mode, crew size,
process maturity, number of contractors, and change intensity). Upon request, we apply a value model:
cost per hour of downtime, incident/failure frequency, response time “before/after”, cost of unplanned work, documentation effort.
Practical scenarios (how it works in the real world)
- Scenario 1: connectivity incident / suspected compromise
The system records the event; AI filters noise and prioritizes the genuine threat. Next — step-by-step guidance: which segments to isolate,
which logs to review, and which actions are safe in the current operating mode. Infrastructure maps and configurations are available immediately — no guesswork.
- Scenario 2: updates and vulnerabilities
You see where versions are outdated and components are risky. Update planning is tied to criticality. You avoid “one forgotten node becomes an entry point”,
and you have evidence: what was updated, when, why and by whom.
- Scenario 3: contractor or crew change
Access, accountability, procedures and documentation are not lost. New teams ramp up faster and make fewer mistakes. The Passport becomes the standard for handover.
- Scenario 4: inspection preparation / insurance case
No need to “collect from people and folders”. A structured pack is produced: architecture, controls, evidence and change history — reducing financial and reputational risk.
- Scenario 5: shipyard refit and change control
During works, the as-built changes are captured: what was added, retired, or reconnected. After completion, you don’t get “new unknowns” —
you get an updated model ready for operations and control.
- Scenario 6: sudden failure of a critical node (navigation/network/service subsystems)
The team immediately sees dependencies, affected segments and applicable procedures. AI suggests diagnostic priorities, while the Passport provides exact configurations and change history.
What we need from the client and how quickly you see the first results
Client inputs
Inputs are provided according to an agreed checklist, typically including:
- list of IT/OT systems and equipment, network diagrams (if available), IP addressing and segmentation;
- software/firmware/services inventory and accounts (within the agreed scope);
- design, operational and service documentation; contractor reports (if available);
- process and role details: responsibilities, authorities, procedures, onboard and shore contacts;
- contractor information, remote-access domains, and service/update practices.
If required, we start with a minimum viable dataset to deliver value quickly,
and expand the model as the client is ready.
How quickly results appear
Work is delivered iteratively:
- initial structure: vessel → systems → segments → key assets;
- baseline documentation pack and diagrams;
- accountability model and procedures;
- connection of telemetry/event sources (where applicable);
- AI alerting and response playbooks enabled;
- continuous refinement and development.
Practical value appears early: a unified register, diagrams, order, risk visibility and change governance.
Support formats (SLA) and development options
Support options
Support and further development are delivered under a separate agreement and typically include:
- keeping the asset database, documentation and diagrams current as changes occur onboard;
- version/vulnerability governance and remediation recommendations;
- crew and shore team consultations on operation and incident response;
- regular reports under an agreed template and incident/failure reviews;
- feature development for new requirements.
SLA levels are tailored to client needs: from “on-demand” support to fixed response procedures and regular reporting.
Development and integrations
As the system matures, we can expand it with:
- additional telemetry and event sources;
- integration with SIEM/log management, monitoring platforms and network sensors;
- expanded AI scenarios (incidents, failures, anomalies, changes);
- checklists for shipyards and contractors;
- inspection/audit packages aligned to specific standards and owner requirements.
Solution delivery formats (4 models)
1) Development based on client-provided data (remote)
The client provides initial technical information about the vessel’s software-hardware environment, including technical documentation,
and organizational inputs for cybersecurity governance: roles, responsibilities, authorities, procedures, contractors, and remote-access domains.
Information is provided via an approved list (questionnaire / checklist).
Service delivery model: Private SaaS (single-tenant):
we deploy and operate a dedicated application instance in a containerized hosting environment, and the client receives secure remote access
(including via VPN).
On our side, we:
- produce digital structural diagrams and an as-is architecture model;
- populate the database (assets, configurations, versions, documentation);
- define a practical set of baseline organizational and technical controls, plus procedures and playbooks;
- deploy a dedicated application instance as Private SaaS and provide secure access to the application and data (VPN).
Ongoing support is provided under separate agreements (SLA/support/development), including data updates,
change governance, consultations, feature development and integrations.
2) Development + on-site vessel assessment
Includes everything in model 1, plus:
- an on-site assessment onboard the vessel (fact gathering, diagram validation, review of current controls and processes);
- a cybersecurity status report and required measures (priorities, action plan, recommendations);
- deployment on the client’s computing platform and initial setup / commissioning.
3) Full cycle: supply/configuration/support of cybersecurity controls + application integration
- supply and configuration of cybersecurity controls for the vessel;
- implementation of organizational and technical measures onboard;
- integration of the application into the cybersecurity environment (event/status collection, monitoring, response processes);
- coordination between onboard and shore teams (notification channels, incident routing, roles, procedures).
4) Tailored mix (recommended)
A flexible combination of models 1, 2 and 3 to fit client objectives: from a Digital Technical Passport to a full cyber protection domain,
with a scalable scope as processes mature and budgets evolve. Engagement is possible at any stage:
design, shipyard build, refit, repair, operations.
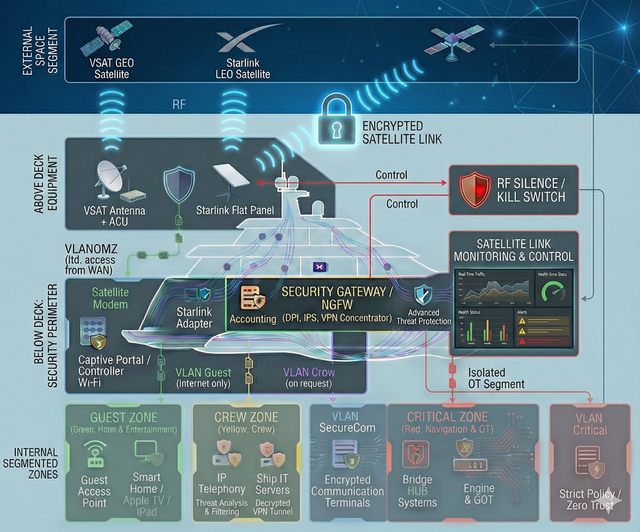
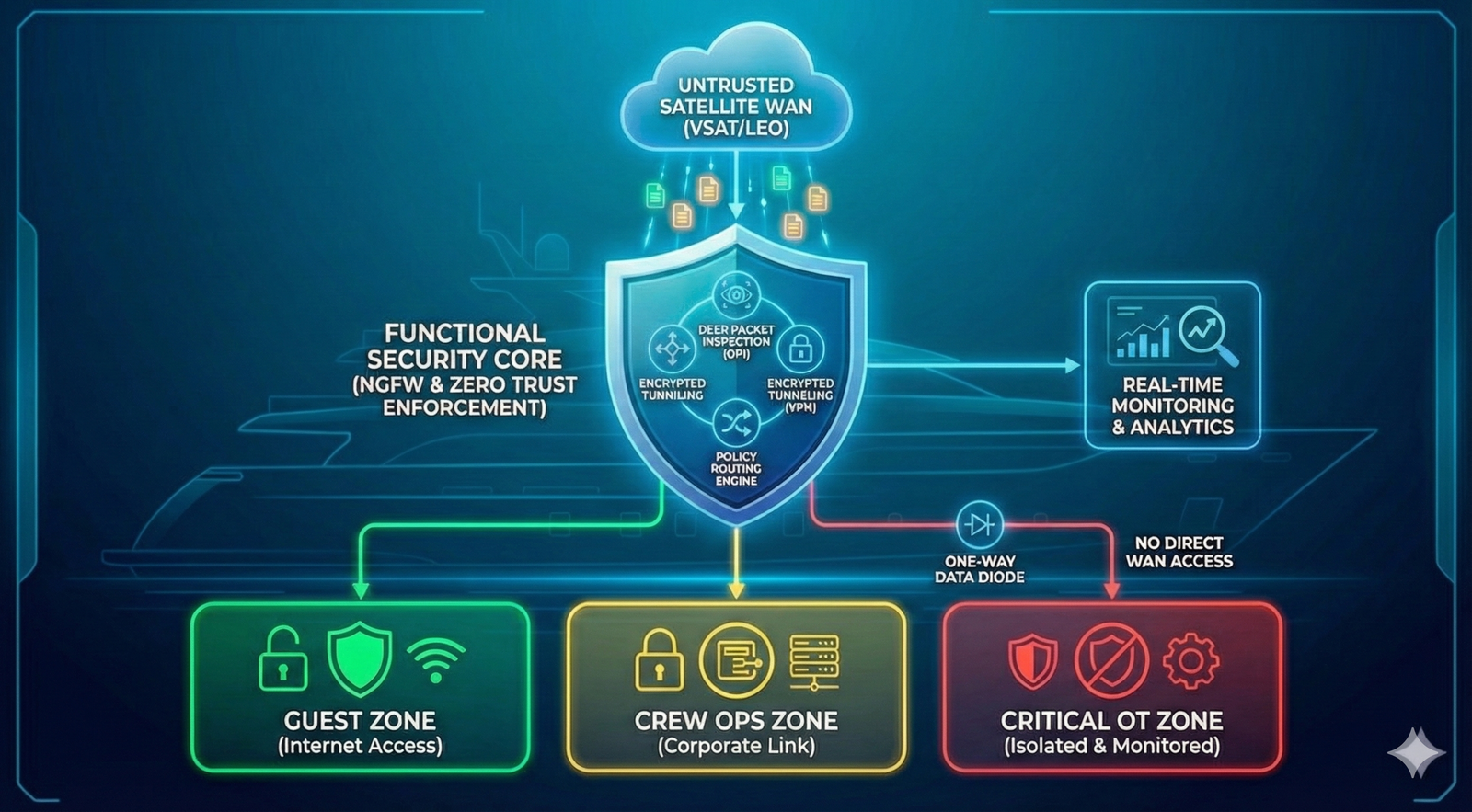
Vendor policy and architecture (3 approaches)
Technology stack selection depends on budget and risk strategy:
-
Enterprise: Palo Alto / Fortinet / Cisco, etc.
Pros: unified ecosystem, vendor support, out-of-the-box AI capabilities, compliance alignment. Cons: high TCO, vendor lock-in, sanctions/geopolitical risks.
-
Open Source: pfSense/OPNSense, Suricata, Zeek, etc.
Pros: no license fees, independence, transparency. Cons: requires high expertise (provided by our team).
-
Hybrid (recommended): combining Enterprise and Open Source at different security layers.
Pros: budget optimization, reduced dependency, avoidance of monoculture as an additional security layer, flexible modernization and expansion.
Deliverables
- a Digital Technical Passport web platform tailored to a specific vessel;
- a database of assets, configurations, versions and documentation;
- digital diagrams / structural models of onboard digital infrastructure;
- baseline controls and procedures / response playbooks;
- (for models 2/3) an assessment report and/or cybersecurity integration;
- a continuously updated single source of truth for shipowners / masters / shore teams: what you have, how it is built, what changed, what risks exist, and what to do.
Next step (how to start)
- agree on the delivery model (1–4) and the required input set;
- define the vessel lifecycle stage (design/shipyard/refit/operations);
- confirm the work plan and deliverables;
- start development and onboarding for your vessel.